Buffer in C Programming Explained with Examples and Safety T
Learn how buffers work in C programming, types of buffers, stdio buffering modes, controlling I/O with setvbuf, and avoiding performance pitfalls.
Introduction to Buffers in C Programming
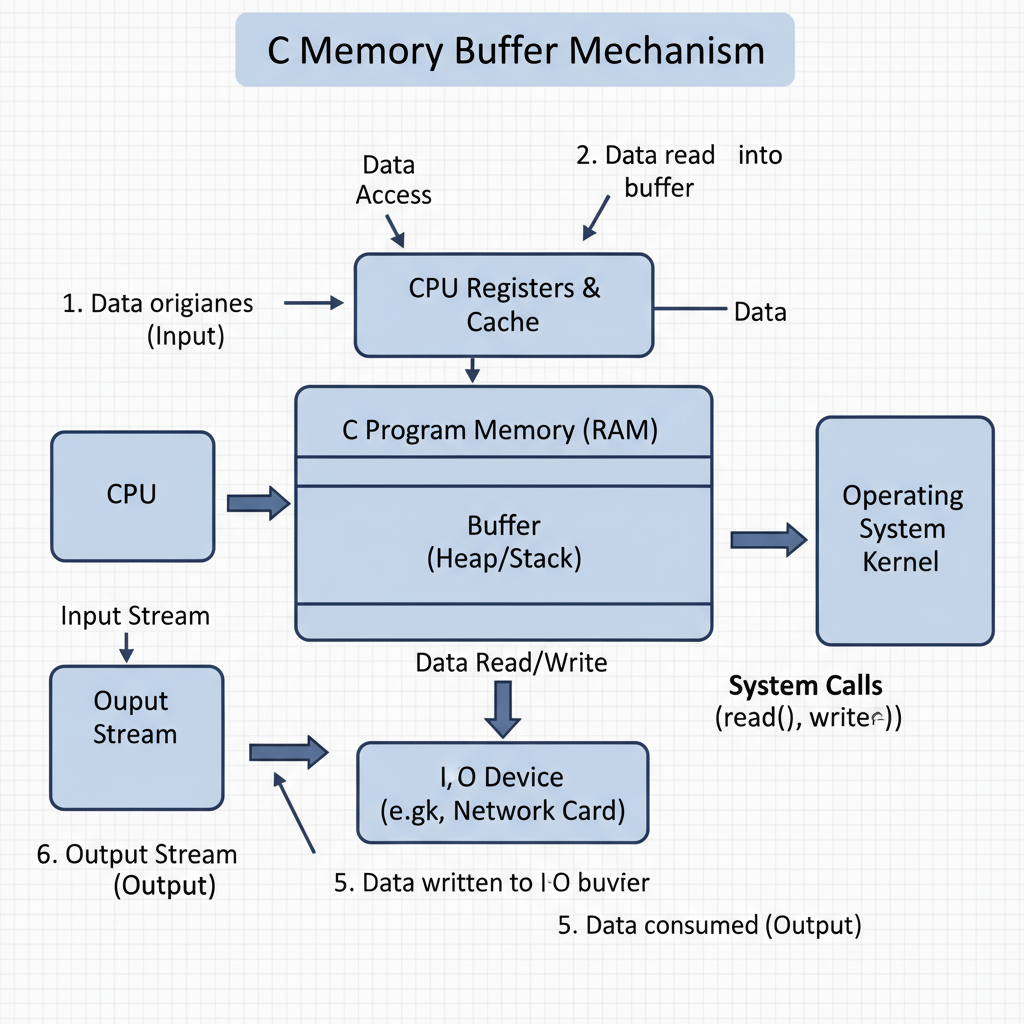
In C programming, a buffer is a temporary memory space crucial for efficient input/output (I/O) operations. A C buffer stores data while it is transferred between a program and an external source or destination—such as a disk, network socket, or terminal. This buffering mechanism bridges speed differences between two operations, prevents the CPU from idling during slow I/O, and processes data in optimized batches rather than one item at a time.
Buffers are especially valuable when input and output devices operate at different speeds—for example, when reading from a slow disk drive into a fast CPU process. By smoothing speed discrepancies, buffers enable smoother, faster programs.
---
How Buffers Work in Memory Management
In C, a buffer is typically a section of memory represented as an array. When you read from an input device, the runtime library often loads data into a buffer before your program processes it. Writing data generally also first places that data into a buffer before it is flushed to the actual device.
The standard C library automates most buffering, but you can configure the behavior. Buffers operate in this general sequence:
- Allocate a block of memory.
- Fill the buffer with incoming data or staged output.
- Flush the buffer to the destination device when full or when explicitly requested.
---
Types of Buffers in C
Although “buffer” is a generic term, there are distinct types in C programming, each serving different purposes:
- Input buffer – Stores data being read in before it’s processed.
- Output buffer – Holds data ready to be sent out.
- Intermediate buffer – Used internally to hold data temporarily during computation.
| Type | Purpose | Example |
|---|---|---|
| Input Buffer | Stores incoming data awaiting processing | Keyboard entry via stdin |
| Output Buffer | Temporarily stores data before writing to output device | stdout printing |
| Intermediate Buffer | Holds data for temporary processing in memory | Sorting algorithms |
---
Standard Input/Output Buffering
The C standard I/O library (`stdio.h`) implements stream-based buffering to improve performance. Every `FILE*` object such as `stdin`, `stdout`, or `stderr` has an associated buffer.
- `stdin` – Generally line-buffered when connected to a terminal.
- `stdout` – Line-buffered to a terminal, fully buffered when redirected to a file.
- `stderr` – Typically unbuffered for timely error reporting.
---
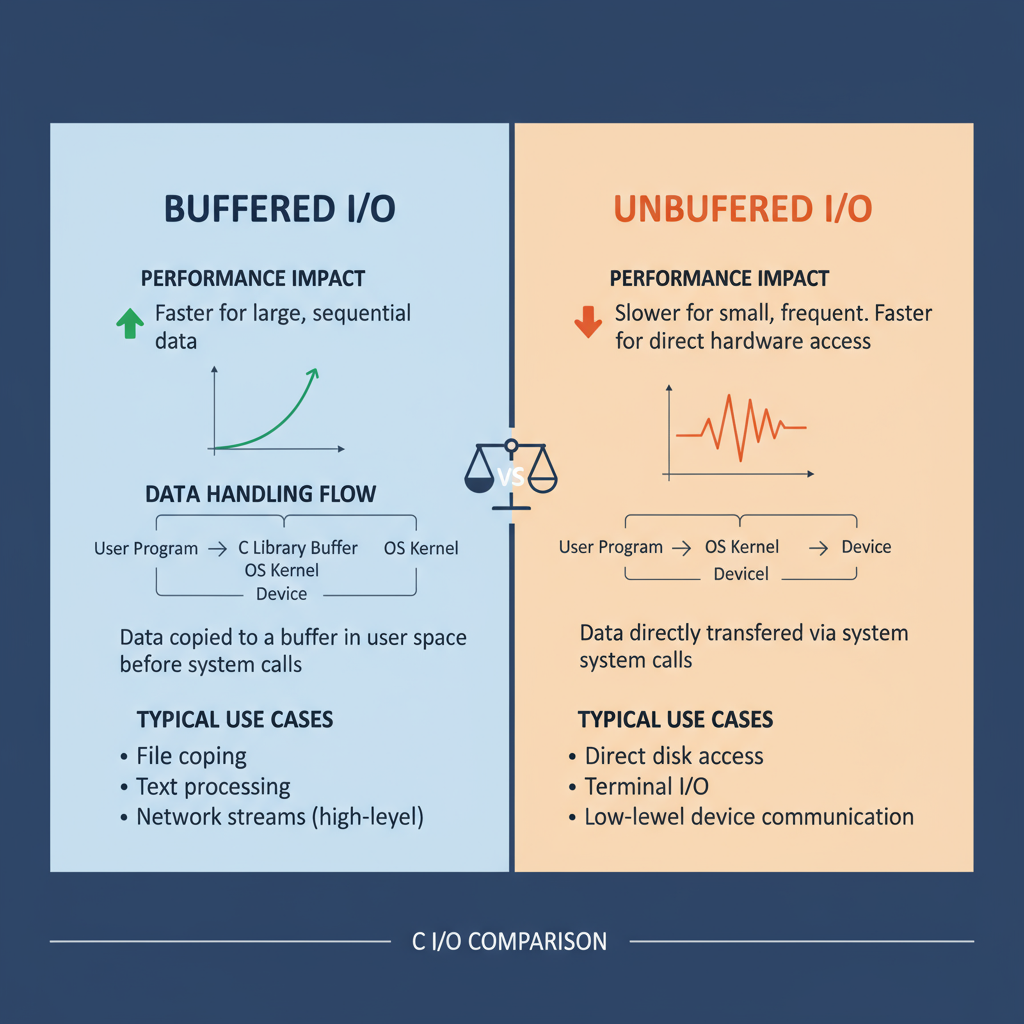
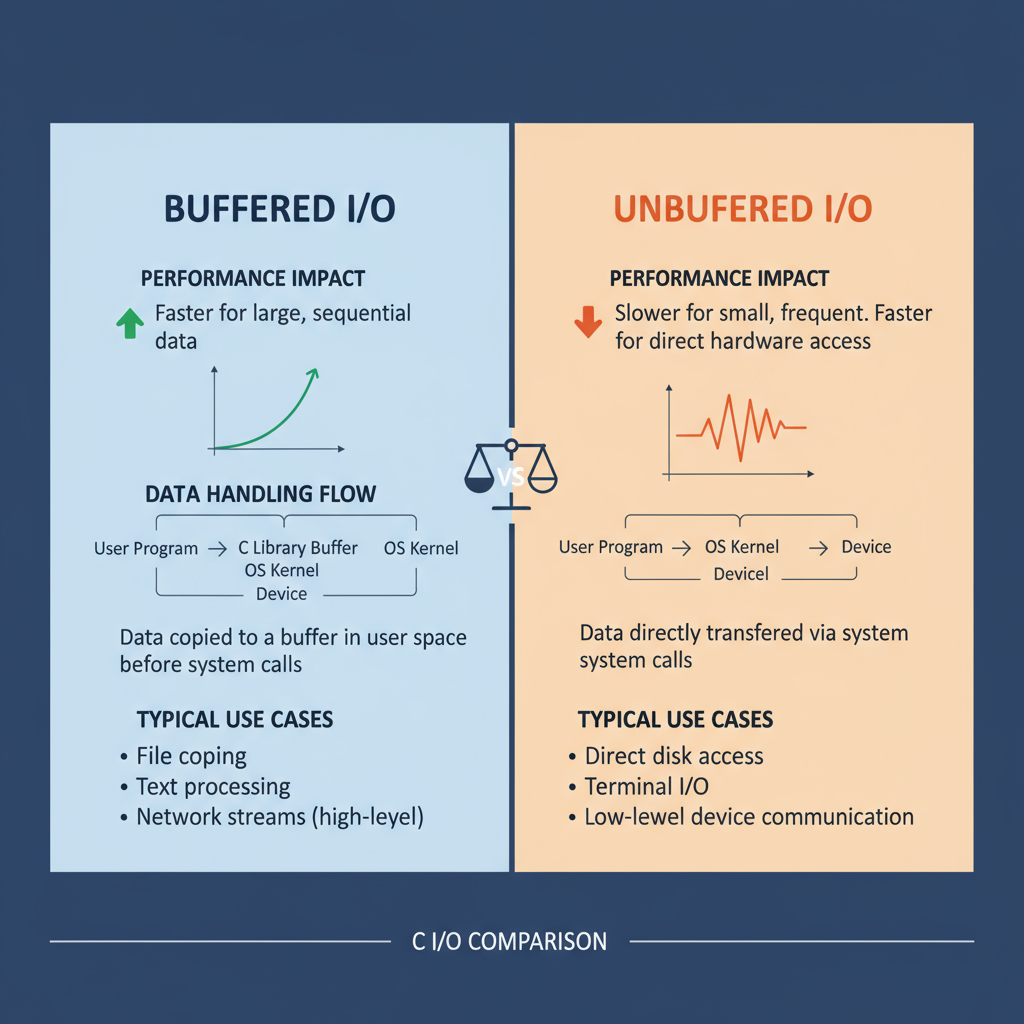
Buffered vs Unbuffered I/O
Buffered I/O: Reads or writes large blocks of data at once, minimizing system calls and improving speed.
Unbuffered I/O: Writes data immediately with no intermediate storage, ensuring prompt output but potentially reducing performance.
Example:
#include
int main() {
printf("Buffered output");
// Without flush here, the above might not appear immediately
fprintf(stderr, "Unbuffered error message\n");
return 0;
}Calling `fflush(stdout)` forces a buffered stream to flush its contents immediately.
---
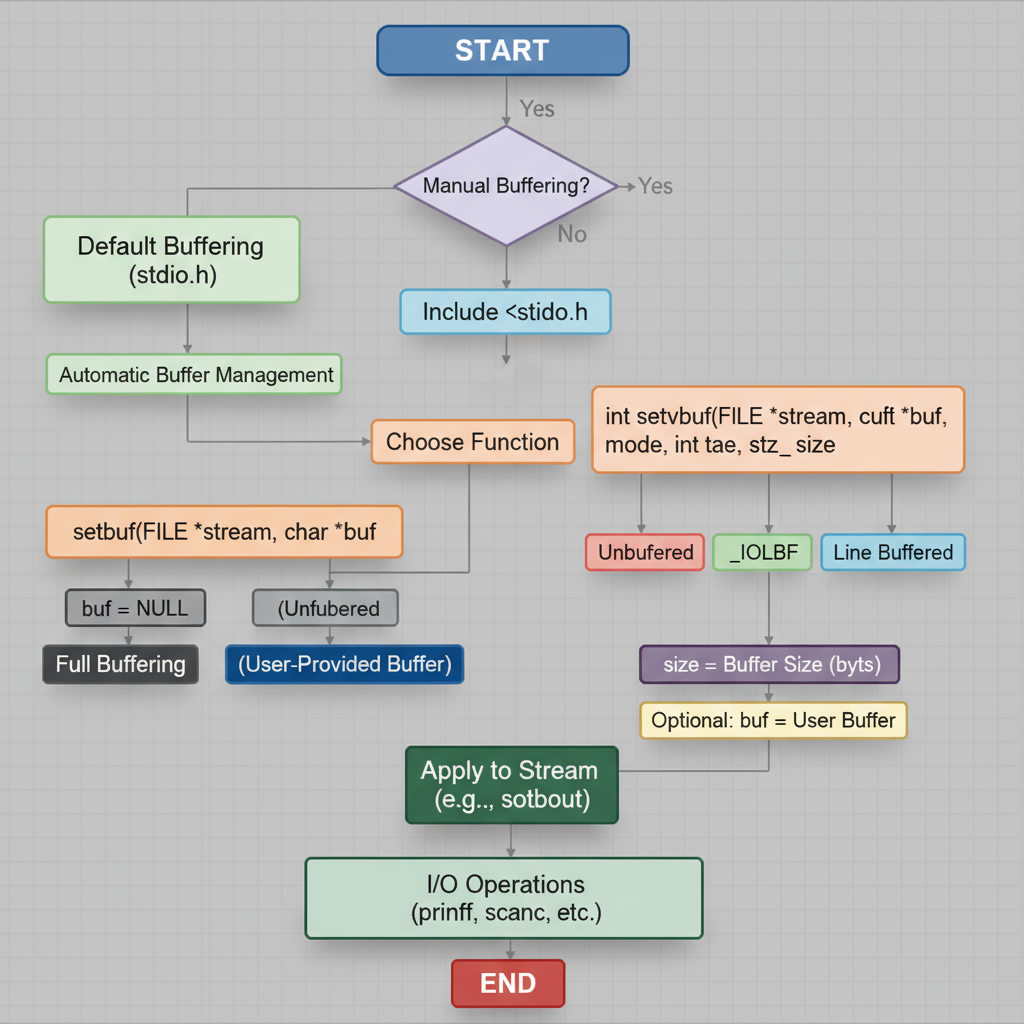
Using `setbuf()` and `setvbuf()` to Control Buffering
C provides functions to control buffering behavior:
- `setbuf(FILE stream, char buffer)` – Assigns a buffer or disables buffering by passing `NULL`.
- `setvbuf(FILE stream, char buffer, int mode, size_t size)` – Allows full (`_IOFBF`), line (`_IOLBF`), or no (`_IONBF`) buffering with a specified size.
Example:
#include
int main() {
char buf[1024];
FILE *fp = fopen("log.txt", "w");
setvbuf(fp, buf, _IOFBF, sizeof(buf)); // Full buffering with custom size
fprintf(fp, "Logging some data...");
fclose(fp);
return 0;
}---
Understanding and Preventing Buffer Overflow
A buffer overflow occurs when writing beyond the allocated space. This corruption can cause crashes, unpredictable results, and serious security vulnerabilities.
Example of unsafe code:
char buf[10];
strcpy(buf, "This is a very long string!"); // Dangerous!---
Safe Practices for Buffer Management
You can reduce overflow risks through these practices:
- Always validate data length before writing to a buffer.
- Use safer, bounded versions of standard functions.
- Prefer functions like `fgets()` over `gets()`, `strncpy()` over `strcpy()`, and `snprintf()` over `sprintf()`.
- Apply compiler protections such as `-fstack-protector`.
| Unsafe Function | Safer Alternative |
|---|---|
| gets() | fgets() |
| strcpy() | strncpy() |
| sprintf() | snprintf() |
---
Dynamic Buffers vs Static Buffers
C buffers can be:
- Static buffers – Fixed-size arrays known at compile time.
- Dynamic buffers – Created at runtime with `malloc()` or similar, offering flexibility but requiring manual memory management.
// Dynamic allocation example
char *buf = malloc(1024);
if (buf) {
// use the buffer
free(buf);
}---
Reading and Writing with Buffers
Safe input/output functions include:
- `fgets()` – Reads a line into a buffer with automatic bounds checking.
- `fread()` – Reads binary data blocks.
- `fwrite()` – Writes binary blocks from a buffer.
Example:
#include
int main() {
char buf[50];
FILE *fp = fopen("data.txt", "r");
if (fp) {
if (fgets(buf, sizeof(buf), fp)) {
printf("Read: %s\n", buf);
}
fclose(fp);
}
return 0;
}
---
Performance Considerations
The choice of buffer size significantly affects performance:
- Disk I/O often benefits from larger buffers, reducing read/write requests.
- Network I/O may be constrained by protocol or packet size limits.
Balance memory usage with the desired speed, profiling different sizes for optimal performance.
---
Debugging Buffer Issues
Troubleshooting buffer-related issues may involve:
- Static analysis – Tools like `clang-tidy` or `cppcheck`.
- Runtime checks – With Valgrind or AddressSanitizer.
- Assertions/logging – To confirm expected sizes at runtime.
- Compiler warnings – Enable verbose warnings with `-Wall -Wextra`.
---
Summary and Best Practices for Buffers in C
Buffers in C are the backbone of efficient data handling for both text and binary operations. Proper use accelerates I/O and avoids data loss, while poor management—especially neglecting bounds checking—can lead to security flaws.
Key takeaways:
- Always protect against overflows by checking bounds.
- Use safe, bounded functions for all string/memory operations.
- Match buffer size to performance goals without over-allocating.
- Adjust buffering modes with `setvbuf()` when necessary.
- Manage dynamic buffers carefully to avoid memory leaks.
By understanding and applying these C buffer management principles, you'll create faster, safer, and more portable applications. Start experimenting with different buffer configurations in your own C projects to see measurable performance and reliability improvements.