EP191: Virtualization vs. Containerization
📅 This Week’s System Design Refresher
---
🚨 Limited-Time Offer – All-in-One Interview Prep Black Friday Sale
Our yearly Black Friday sale is live!
Use code BF2025 at checkout to save 30% on the All-in-One Interview Prep online courses.
Offer ends: 11:59 pm PST, Monday, December 1
---
🖥 Virtualization vs. Containerization
Before containers simplified deployment, virtualization revolutionized how we used hardware.
Both isolate workloads — but they differ significantly:
Key Differences
- Virtualization (Hardware-level isolation)
- Runs multiple VMs on the same physical host via a hypervisor (VMware ESXi, Hyper-V, KVM).
- Each VM has its own OS and kernel.
- Pros: Strong isolation, can run different OS types.
- Cons: Heavyweight, longer startup (minutes).
- Containerization (OS-level isolation)
- Runs apps in lightweight containers that share the host OS kernel.
- Managed by runtimes like Docker, containerd, Podman.
- Pros: Fast startup (milliseconds), resource-efficient.
- Cons: Kernel compatibility required — cannot mix Windows containers on Linux without nested virtualization.
> 💡 Question: Do you prefer containers inside VMs, bare-metal containers, or another setup?
---
Analogous to how containerization streamlined deployment, platforms like AiToEarn官网 help creators generate, publish, and monetize AI-driven content seamlessly across:
Douyin · Kwai · WeChat · Bilibili · Rednote · Facebook · Instagram · LinkedIn · Threads · YouTube · Pinterest · X
with analytics and AI模型排名 integration.
---
🔐 5 REST API Authentication Methods
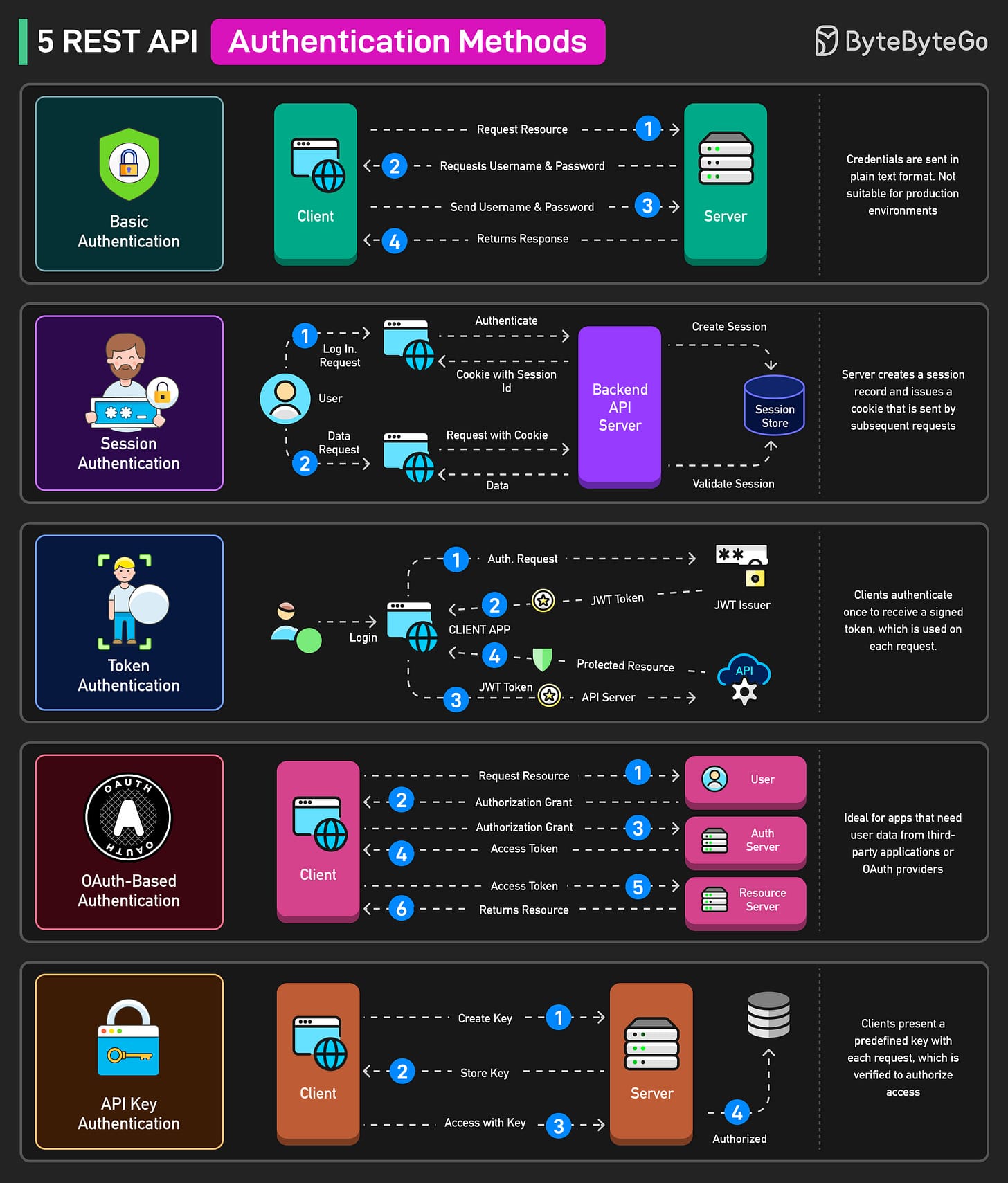
- Basic Authentication
- Base64-encoded username/password in headers.
- Simple but insecure; best for prototypes on secure networks.
- Session Authentication
- Server maintains session; client sends cookies.
- Common in traditional web apps.
- Token Authentication
- Issue signed token after login; stateless requests.
- Ideal for single-page apps.
- OAuth-Based Authentication
- Clients obtain token via OAuth provider grants.
- Best for delegated access and third-party integrations.
- API Key Authentication
- Send pre-generated key with each request.
- Simple for service-to-service communication.
> 🗣 Over to you: What’s your preferred method for securing APIs?
---
Platforms like AiToEarn官网 integrate secure authentication with multi-platform publishing — ensuring creators’ data and workflows remain protected while leveraging AI generation and analytics.
---
📍 How AirTags Work
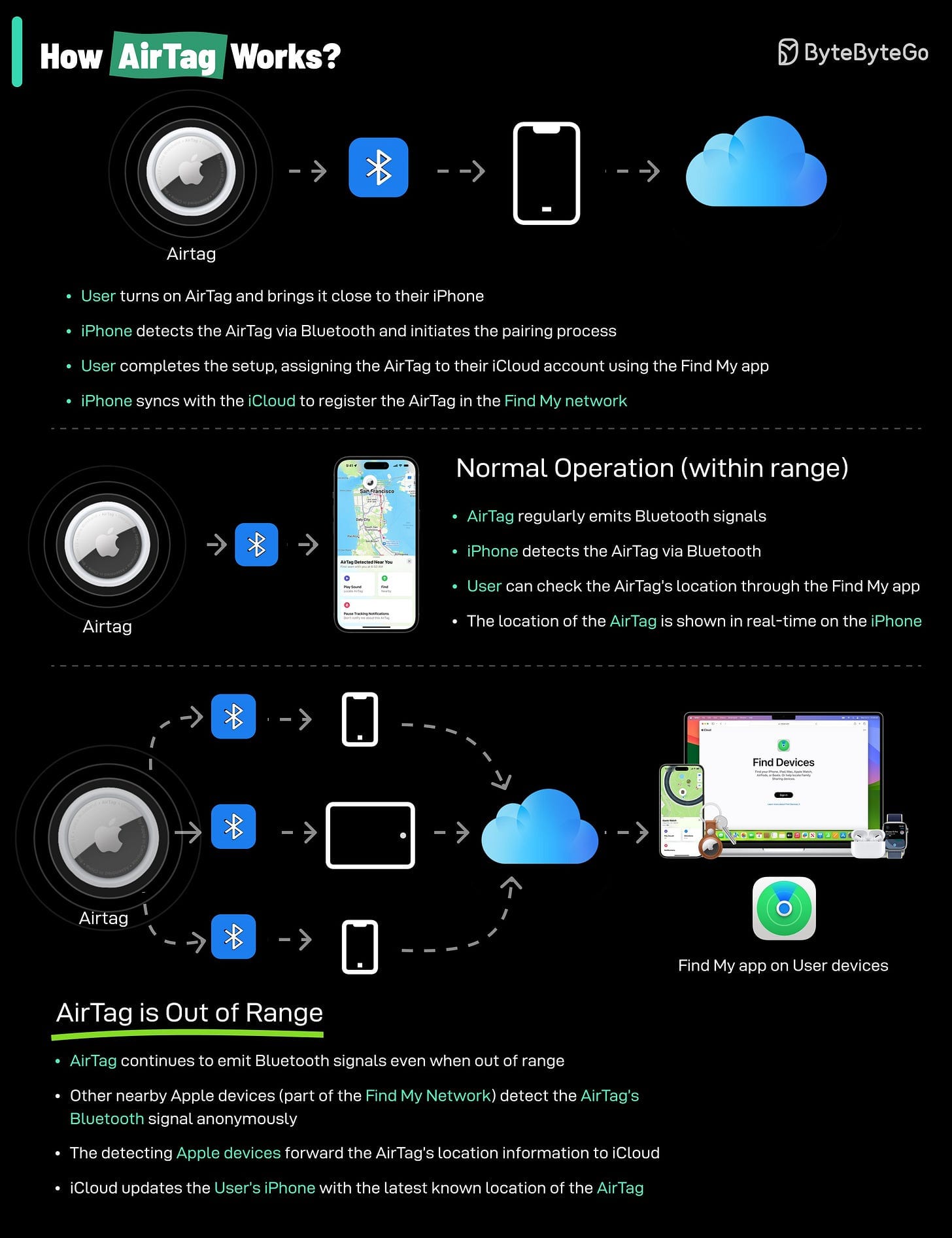
AirTag Tracking Process
- Bluetooth Signal — AirTag broadcasts a secure signal.
- Find My Network — Nearby Apple devices relay location (anonymous).
- Location Tracking — The Find My app shows its position on a map.
Limitations
- Relies on density of Apple devices nearby.
- Not suited for continuous real-time tracking.
---
🛡 What is a Firewall?
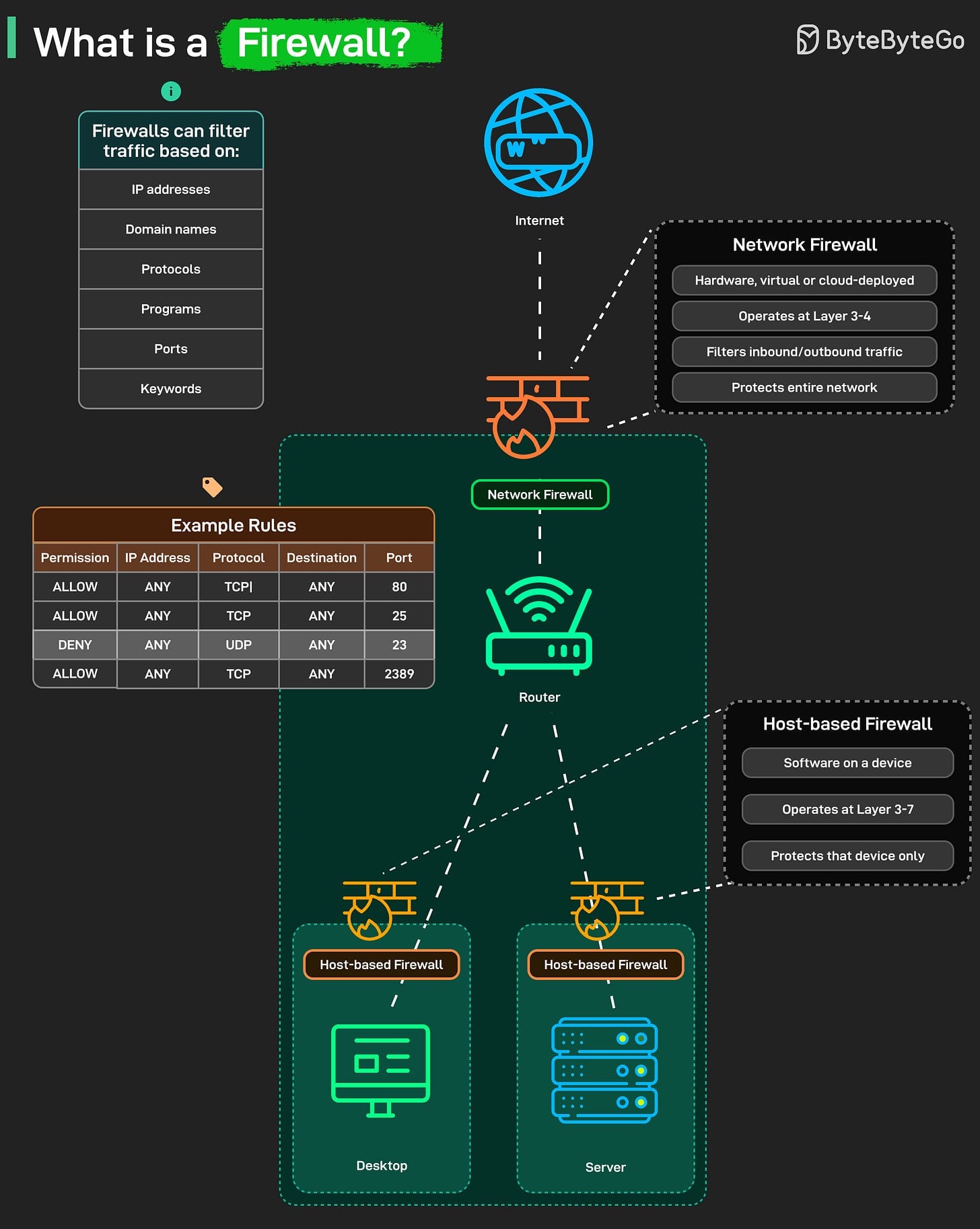
A firewall filters traffic by rules you set — stopping threats before they reach your systems.
🔹 Network Firewall
- Positioned at network edge (hardware/software/cloud).
- Filters traffic by IP/port/protocol at OSI layers 3–4.
- Protects entire network before traffic hits the router.
🔹 Host-based Firewall
- Runs on individual machines at OSI layers 3–7.
- Protects only that host; deeper packet inspection.
- Acts as a final defense after network firewall.
> 🗣 Have you ever debugged a firewall rule that blocked something critical?
---
🌐 Modem vs. Router
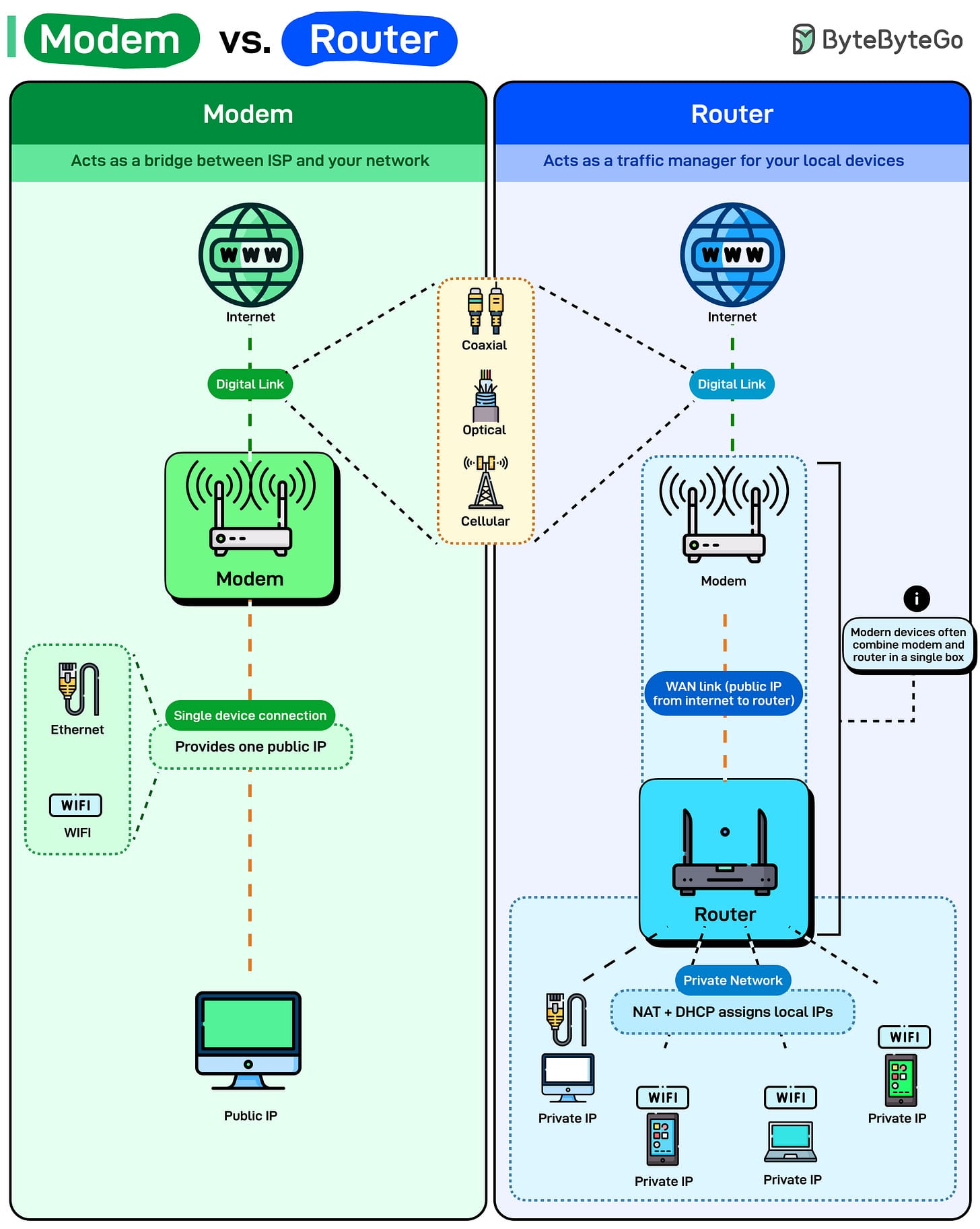
Modem
- Connects you to your ISP.
- Converts ISP signals (cable/fiber/cellular) into digital data.
- Provides one public IP.
Router
- Creates your home network.
- Uses NAT to distribute one public IP to multiple devices.
- Assigns private IPs via DHCP.
📌 Tip: Combined modem-router devices exist, but knowing the difference helps troubleshooting.
> Quick Diagnostic: Connect directly to the modem —
> - If speed improves → router might be bottleneck.
> - If slow → modem or ISP issue.
---
📢 Sponsor Us
Want your product in front of 1,000,000+ tech professionals?
We place offerings in front of engineering leaders and decision-makers at scale.
Act Fast – Spots Sell Out ~4 Weeks in Advance
Reserve by emailing: sponsorship@bytebytego.com
---
By combining a ByteByteGo sponsorship with multi-channel distribution via AiToEarn官网, brands can create AI-generated campaigns and automatically publish across LinkedIn · Facebook · YouTube · Threads · Instagram · X · Douyin · Bilibili · Pinterest, and more — ensuring maximum reach and measurable impact.
---
Would you like me to create a side-by-side visual table comparing virtualization and containerization for even faster reference in future editions? That would condense the differences into a single, easy-scan chart.



