# ICBC e-Qiyan — Fine-Grained Permission Management for Digital R&D Transformation
**Date:** 2025-11-29 10:16
**Location:** Zhejiang

Under the **digital transformation** strategy, the **Industrial and Commercial Bank of China (ICBC) Software Development Center** is advancing digital R&D management, aligned with the “Digital ICBC” development goal.

---
## Background
The ICBC Software Development Center has been implementing an **integrated approach** combining:
- **Touchpoint integration**
- **Service aggregation**
- **Operational convergence**
Focusing on **user-centric design**, the center consolidated tool capabilities into the **one-stop R&D management portal** — *ICBC e-Qiyan*.
### Deployment
The platform now serves **seven institutions**:
- Head Office Financial Technology Department
- Software Development Center
- Business R&D Center
- Data Center
- Platform Finance Development Center
- Transaction Banking Center
- ICBC Technology
Its users include product managers, architects, project managers, developers, testers, etc., enabling **end-to-end R&D management services**.
### Challenge
Growing cross-institution adoption revealed **limitations** in:
- Cross-organization collaboration
- Fine-grained authorization control
Additionally, the **cybersecurity threat landscape** demands stronger protection to secure sensitive data and critical business processes.
---
## Construction Approach
The center built a **fully configurable, scenario-based menu permission management system** with **four-dimensional fine-grained authorization**:
1. **Institution Dimension** — Data isolation between institutions.
2. **Department Dimension** — Hierarchical inheritance plus independent configuration.
3. **Role Dimension** — Standardized templates for rapid authorization.
4. **User Dimension** — Micro-adjustments for personalized needs.
**Delegated authorization** enables assigning permissions by role or function, with options to modify, suspend, or terminate.
A **Global Permission Activity Log Center** ensures **traceability and permanent retention** for all changes.
---
## Implementation Achievements
### Configurable Menu Permission Management — Efficiency Gains
- **Dynamic design** — Supports menu registration, activation, and deactivation **without coding**.
- **Visual interface** — Configure menus, icons, behaviour, and guidance notes in real time.
- **Layered security** — Permissions applied at institution, department, role, and user levels.
- **Compliance & Flexibility** — Combines standardized role templates with user-specific adjustments.
- Updates flow through **online approval workflows** for full traceability.

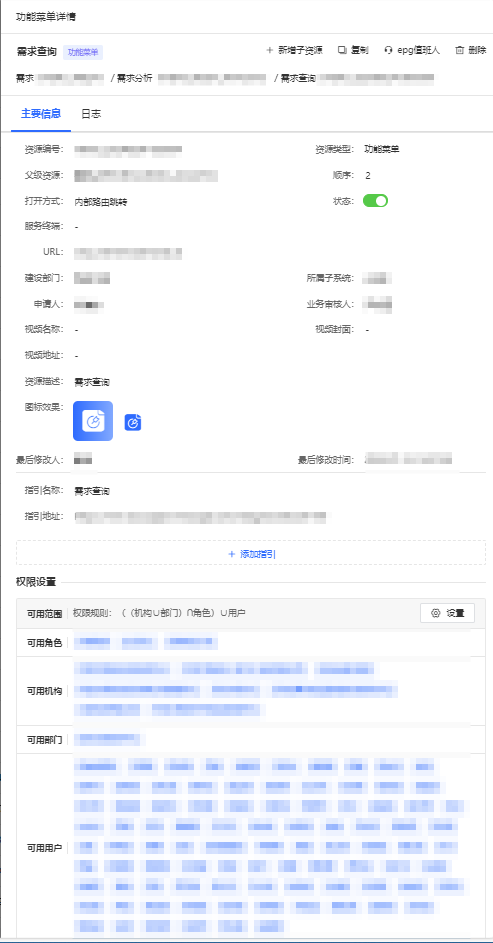
*Figure 1: Menu Permission Management*
---
### Fine-Grained Permission System — Security Enhancements
#### Automated Permission Lifecycle
Integration with HR systems ensures:
- **Onboarding** — Auto-assignment via templates aligned with position.
- **Transfers** — Instant revocation and new assignment based on department change.
- **Resignation** — Immediate account freeze and permission removal.
---
## Four-Dimensional Linked Access Control
ICBC e-Qiyan's framework includes:
1. **Organization Dimension** — Strict data isolation; account-to-organization binding.
2. **Department Dimension** — Structured inheritance; permissions update automatically on transfers.
3. **Role Dimension** — Predefined templates for R&D positions; batch assignment.
4. **User Dimension** — Personalized adjustments without altering the core structure.
---
## Menu-Level and Operation-Level Control
Dual-level permission management:
- **Menu-Level** — Configure visible menu items per role.
- **Operation-Level** — Three states: invisible, visible-but-disabled, fully operable.
This enforces **least privilege** and prevents unauthorized actions.
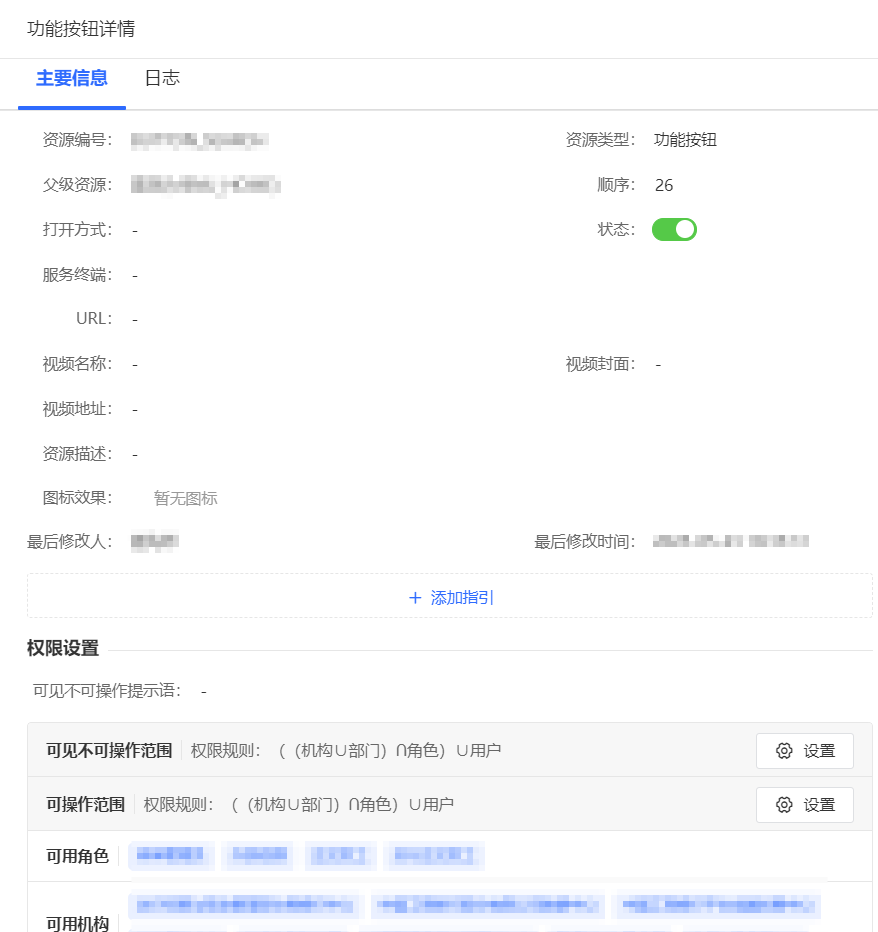
*Figure 2: Operation Button Permission Management*
---
## Online Role and Permission Approval
Entire lifecycle handled online:
- Request submission
- Multi-level approval
- Activation
Ensures efficiency and security.
---
## Authorization Transfer Center — Boosting Collaboration
Accessible via **PC and mobile**:
- Add, query, terminate authorizations
- Notify and review history
- One-click function or role-based transfers
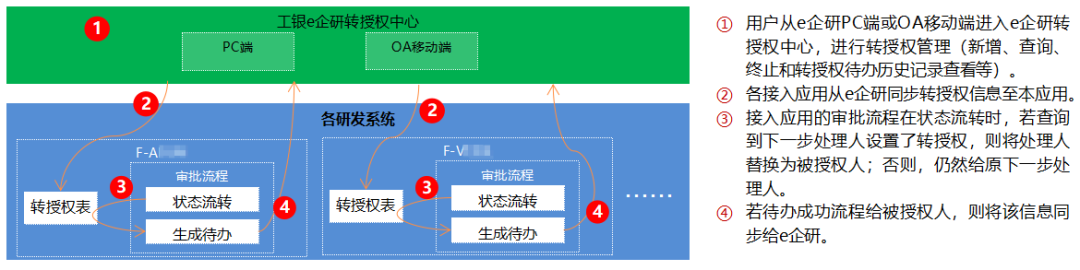
*Figure 3: Authorization Transfer Center Overview*
---
### One-Click Authorization Transfer
Steps:
1. Login to Authorization Transfer Center.
2. Select systems, workflows, or roles to delegate.
3. Choose authorized person.
4. Confirm — workflows route automatically.
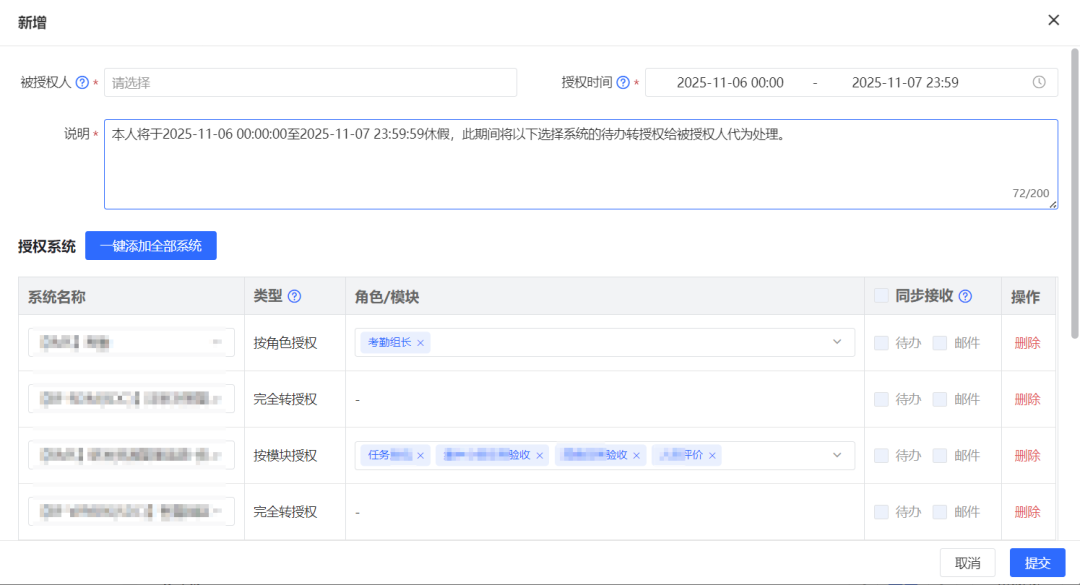
*Figure 4: One-Click Authorization Transfer*
---
### Flexible Authorization Modes
- **Function-Based** — Delegates all workflows for a business function.
- **Role-Based** — Delegates based on approval role; supports time limits.
**Real-time sync** keeps systems secure and up-to-date. All actions are fully logged — including participants, scope, and validity.
---
## Global Permission Action Log Center — Full Traceability
Using **three-dimensional log collection**:
1. **Login Logs** — Record authentication time, device, IP.
2. **Operation Logs** — Track menu access, actions, and data changes.
3. **Request Logs** — Trace API-level data flows, parameters, and statuses.
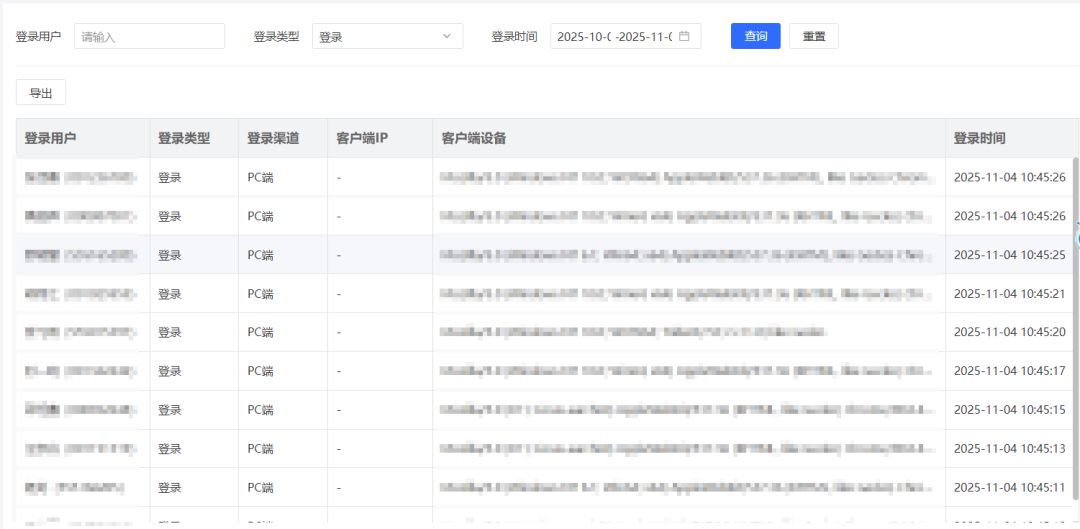
*Figure 5: Login Log*
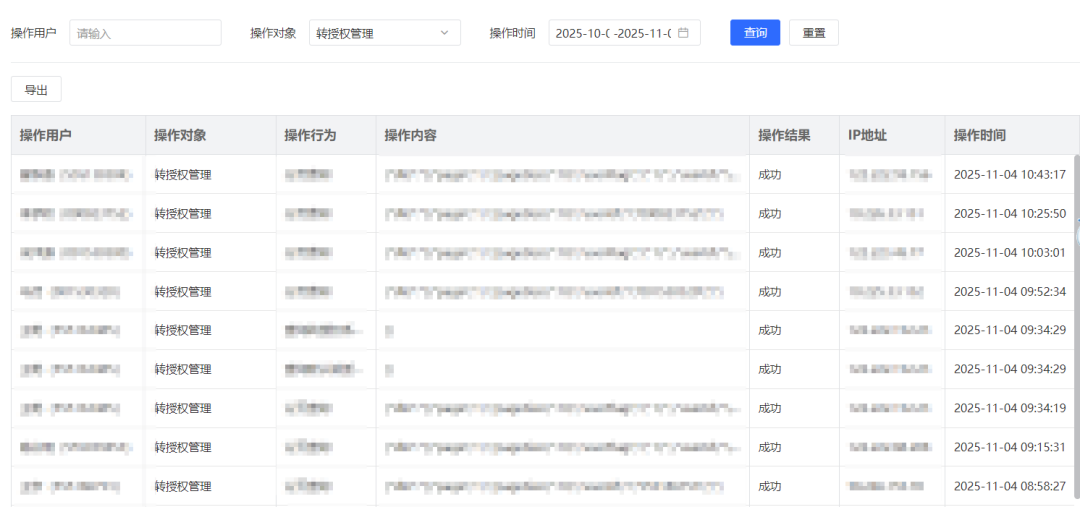
*Figure 6: Operation Log*
---
## Future Outlook
Plans include:
- Enhanced role management
- Adding **“associated organization”** attributes
- Flexibly configuring cross-organization roles
- Improving collaboration efficiency
- Strengthening security measures
---
## Related Reading
- [“In mathematics, Chinese models have never lost”! DeepSeek dominates overnight...](https://mp.weixin.qq.com/s?__biz=MjM5MDE0Mjc4MA==&mid=2651264391&idx=1&sn=0f0166d43be4dd7b0284e474d1c9543a&scene=21#wechat_redirect)
- [The clear-headed Linus: doesn’t use AI programming tools...](https://mp.weixin.qq.com/s?__biz=MjM5MDE0Mjc4MA==&mid=2651264336&idx=1&sn=8584626db0801b92ce2a383d5b592127&scene=21#wechat_redirect)
- [$25,000 for internal company screenshots — losing the job...](https://mp.weixin.qq.com/s?__biz=MjM5MDE0Mjc4MA==&mid=2651264284&idx=1&sn=7b878c189acbc7ab854fe559939e9ae4&scene=21#wechat_redirect)
- [Textbook-style scam in the AI circle...](https://mp.weixin.qq.com/s?__biz=MjM5MDE0Mjc4MA==&mid=2651264132&idx=1&sn=c94bb224a933d7ce2ecc181e4a9e2d40&scene=21#wechat_redirect)
---
**Original:** [Read the original](2651264588)
**WeChat:** [Open in WeChat](https://wechat2rss.bestblogs.dev/link-proxy/?k=2c36b655&r=1&u=https%3A%2F%2Fmp.weixin.qq.com%2Fs%3F__biz%3DMjM5MDE0Mjc4MA%3D%3D%26mid%3D2651264588%26idx%3D3%26sn%3Db4e2b3c7ff6d8da455ab2013f5f66742)
---
## AI-Driven Content Parallel
Platforms like [AiToEarn官网](https://aitoearn.ai/) offer **open-source global AI content monetization**, echoing ICBC's efficiency + security principles.
Key features:
- AI-powered content generation
- Cross-platform publishing — Douyin, Kwai, WeChat, Bilibili, Xiaohongshu, Facebook, Instagram, LinkedIn, Threads, YouTube, Pinterest, X (Twitter)
- Analytics and [AI模型排名](https://rank.aitoearn.ai)
- Secure workflow management
Such tools enable creators to monetize AI creativity with confidence — similar to enterprise-grade permission systems ensuring collaborative safety.




