# Comprehensive Guide to Oracle Database Security Capabilities
## Introduction
In today’s **digital survival landscape**, data has become the **core asset** and lifeline for enterprises.
From mission-critical business data and customer privacy to intellectual property, these valuable resources stored in databases face multiple challenges:
- **External attacks**
- **Internal threats**
- **Compliance failures**
A single breach can cause **massive economic loss**, **severe legal penalties**, and **irreversible reputational damage**.
**Key takeaway:**
Building a **multi-layered defense system** that protects data across its lifespan is **not optional** — it’s a strategic necessity for business survival and growth.
This not only satisfies regulations like **GDPR** and **PCI DSS**, but also earns **customer trust** and ensures **business continuity**.
This article uses **Oracle Database security capabilities** to explore essential skills in database security and analyze gaps with current domestic database solutions.
---
## 1. Security Threats Facing Databases
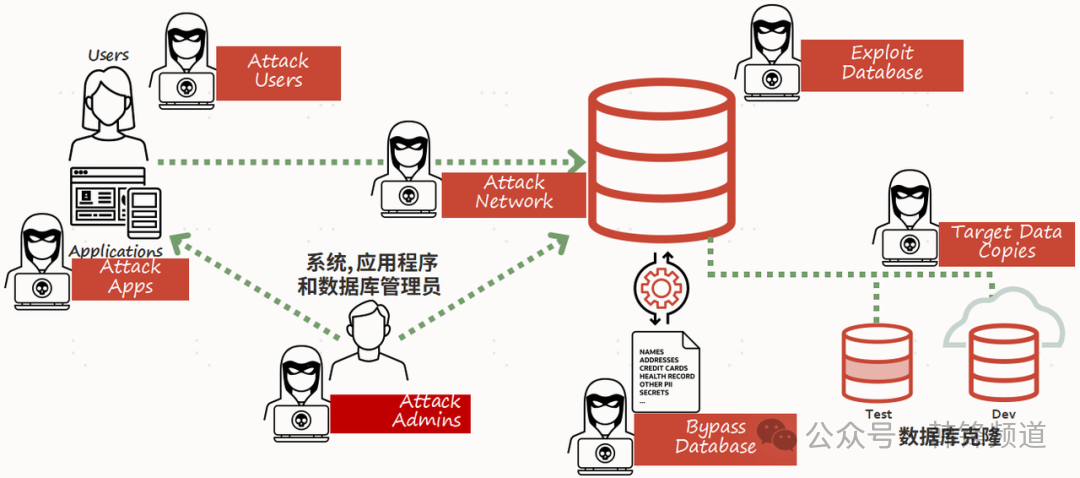
This diagram maps the **multidimensional ecosystem of database threats**.
We detail **five core layers** below:
### 1.1 Endpoint User Layer Penetration
- Attackers impersonate valid users or hijack accounts via trojans.
- Weak passwords and stolen credentials allow them to bypass authentication.
- Once logged in, they exploit **SQL injection** or **privilege escalation** to steal sensitive data.
### 1.2 Application Layer Vulnerabilities
- Applications are frequent attack targets due to coding flaws.
- Exploits include **code injection** and **API abuse** to reach the database layer.
- Static credentials and excessive privileges allow easy pivoting to core data.
### 1.3 Network Transmission Risks
- **Man-in-the-middle** attacks steal or modify unencrypted traffic.
- Attacks may bypass front-end defenses via **direct port scanning** or **brute force**.
### 1.4 Internal Risks from Admin Privileges
- Misuse or theft of admin accounts can cause **unauthorized data changes** or exports.
- Insider threats are notoriously difficult to detect without **privilege separation**.
---
**Best Practices:**
A comprehensive database defense integrates:
- Endpoint identity protection
- Network encryption
- Application hardening
- Privilege governance
Organizations are increasingly adopting **AI-powered monitoring** alongside traditional controls.
> **Tip:** Platforms like [AiToEarn官网](https://aitoearn.ai/) can help content creators distribute security know‑how across multiple global channels efficiently.
---
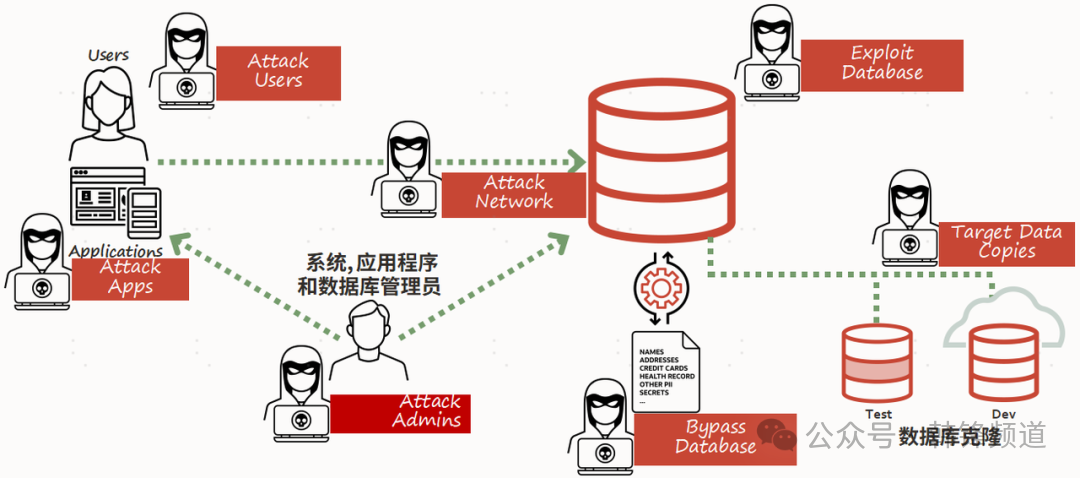
### 1.5 Risks in the Data Lifecycle
- Test/dev **data clones** often have weaker security.
- Vulnerabilities in clone environments can expose production‑level sensitive data.
- Attackers exploit **misconfigurations** or outdated systems to bypass controls.
**Layered defense essentials:**
- **Identity governance**
- **Application hardening**
- **Transmission encryption**
- **Privilege separation** (e.g., Database Vault)
- **Data masking**
- **End-to-end monitoring** (e.g., Audit Vault)
---
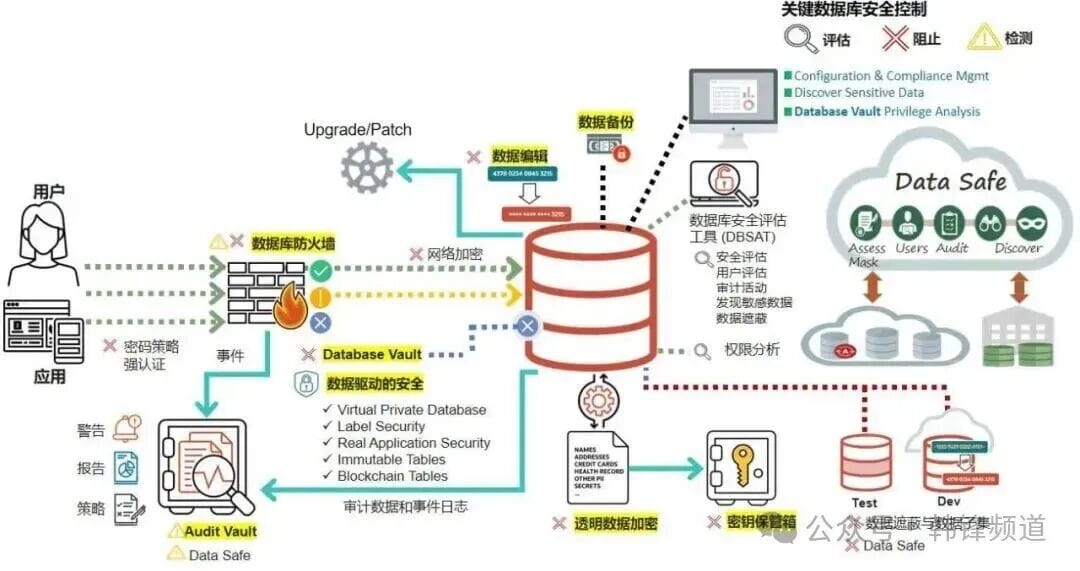
## 2. Oracle Security Capabilities Overview
Oracle’s security design follows **four key principles**:
1. **Defense in Depth** — multiple, layered controls from outer to inner perimeters.
2. **Data-Centric Approach** — focus on protecting **the asset** itself.
3. **Lifecycle Coverage** — from data classification and access control to post-event audits.
4. **Automation & Intelligence** — automated data discovery, privilege analysis, unified management.
---
### 2.1 Oracle Database Firewall
- Monitors and controls **all incoming SQL**.
- Detects **complex SQL injection** through deep syntax analysis.
- Configurable **whitelists**, **blacklists**, and **exception lists**.
- Modes: **Online blocking** or **Passive monitoring**
- Supports **privileged user monitoring** and **compliance reporting** (SOX, PCI DSS).
---
### 2.2 Network Encryption
- End-to-end protection via **Native Network Encryption** or **TLS/SSL**.
- Uses strong encryption (**AES256**) and integrity checks (**SHA256**).
- Transparent to applications; easily enabled for compliance needs.
---
### 2.3 Password Policy
- Enforced via the `PROFILE` configuration.
- Controls complexity, expiration, and failed login lockouts.
- First line of defense for **account credential integrity**.
---
### 2.4 User Authentication
- Supports multiple authentication sources:
- Database username/password
- OS authentication
- Kerberos / PKI / RADIUS
- Tracks **end-user identity** in multi-tier systems for accurate auditing.
---
### 2.5 Privilege Analysis
- Monitors real usage of granted privileges.
- Identifies unnecessary or excessive permissions.
- Enforces **least privilege principle** to reduce attack surface.
---
### 2.6 Database Vault (Separation of Duties)
- Restricts even DBAs from viewing certain sensitive data.
- Uses **realms**, **command rules**, and **factor-based rules** for control.
- Strong compliance support for separation of duties.
---
### 2.7 Data Label Security
- Mandatory row-level controls using **classification labels**.
- Labels match user privileges for data visibility.
- No application code changes needed.
---
### 2.8 Virtual Private Database
- Fine-grained row/column permissions enforced at the kernel level.
- Automatically appends `WHERE` clauses to user queries.
- Transparent, centralized enforcement outside application code.
---
### 2.9 Sensitive Data Discovery
- **Oracle Data Safe** can detect 170+ predefined sensitive data types.
- Methods: Name pattern matching, sampling, relational analysis.
---
### 2.10 Static Data Masking
- Non-production environments get **realistic but fictitious** data.
- Preserves format and referential integrity.
- Protects privacy during dev/test projects.
---
### 2.11 Dynamic Data Masking
- Masks data in **real-time** during query processing.
- Configurable by policy, session context, or role.
- Original data remains intact in storage.
---
### 2.12 Database Auditing
- Monitors and records **all user activity**.
- Supports:
- Statement audit
- Privilege audit
- Object audit
- **Unified Auditing** consolidates audit trails for efficiency and security.
---
### 2.13 Audit Vault
- Collects and encrypts audit logs from multiple sources.
- Real-time analysis with **alerting** on high-risk events.
- Supplies compliance templates (SOX, PCI DSS).
---
### 2.14 Transparent Data Encryption (TDE)
- Encrypts data at rest using AES256.
- Master key stored externally (Oracle Wallet / HSM).
- Minimal performance impact with hardware acceleration.
---
### 2.15 Key Vault
- Centralized management for:
- TDE master keys
- Certificates
- SSH keys
- Passwords
- API tokens
- Supports integration via **KMIP** and **REST API**.
---
### 2.16 Immutable / Blockchain Tables
- **Blockchain Tables**: hash chains for tamper-evidence.
- **Immutable Tables**: insert-only with retention policy.
- Used for audits, compliance, and high-trust applications.
---
### 2.17 Oracle Secure Backup
- Encrypts backups at the host or hardware level.
- Integrates with **RMAN** for end-to-end encryption.
- Role-based access, SSL/TLS secure channels.
---
### 2.18 Configuration & Compliance Management
- Delivered via **Oracle Enterprise Manager** with:
- CIS & STIG benchmarks
- Policy libraries
- Drift detection
- Produces compliance scores and remediation guidance.
---
### 2.19 Patching and Upgrades
- Quarterly **Critical Patch Updates (CPU)** and **Security Patch Updates (SPU)**.
- **Patch Set Updates (PSU)** include stability fixes.
- **OPatch** tool manages install/rollback; supports RAC rolling patches.
- Cloud environments automate patching.
---
### 2.20 Situational Awareness — DBSAT
- **Database Security Assessment Tool**:
- Collector (gathers metadata)
- Reporter (analyzes against best practice)
- Discoverer (identifies sensitive data)
- Output: HTML, Excel, JSON reports with remediation steps.
---
### 2.21 Unified Security Platform — Data Safe
- Security configuration assessments
- Sensitive data discovery
- Static masking
- User-risk analysis
- Activity auditing
- SQL firewall for injection blocking
---
### 2.22 Application Security — RAS
- **Real Application Security**:
- Application users & roles
- Access control lists
- Data realms
- Supports identity propagation in 3-tier architectures.
---
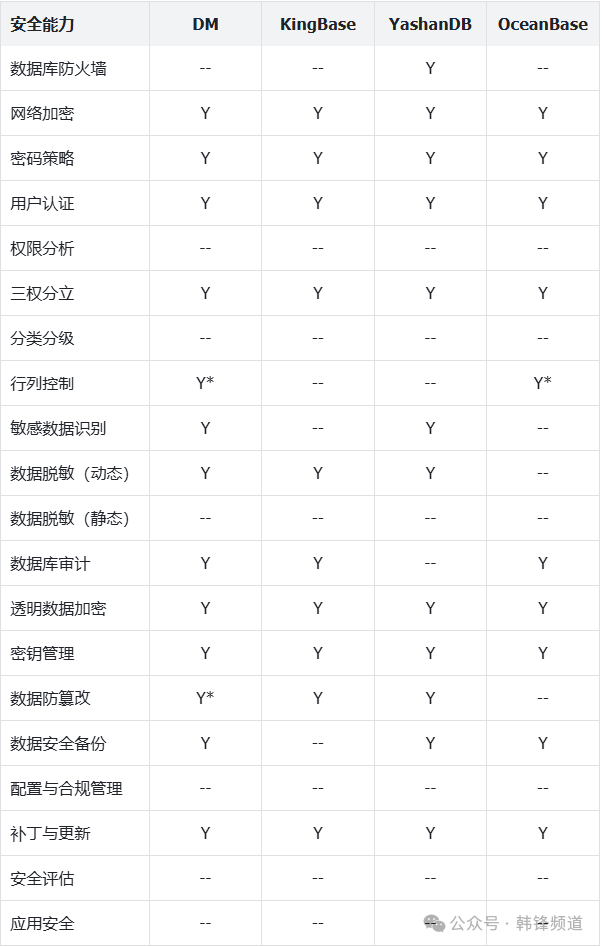
## 3. Domestic Database Security Comparison
Below is a vendor-documented feature comparison of domestic database security vs. Oracle’s capabilities:
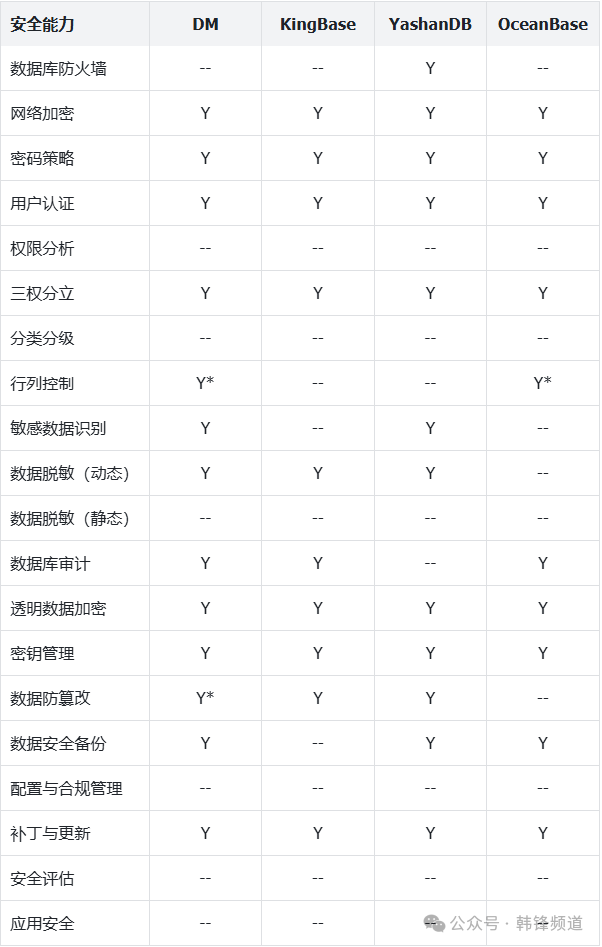
> **Note:** Absence of details does not mean capability is missing; some may be implemented differently, marked as **Y***.
---
## Conclusion
Oracle provides a **comprehensive, layered security model** addressing:
- Threat prevention
- Data classification and masking
- Privilege governance
- Auditing & compliance
- Encryption and secure backups
Open-source platforms like **[AiToEarn](https://aitoearn.ai/)** also illustrate how **centralized management** principles can be applied in other domains — enabling creators to publish AI-generated content across **Douyin, Kwai, WeChat, Bilibili, Xiaohongshu, Facebook, Instagram, LinkedIn, Threads, YouTube, Pinterest, and X/Twitter** with analytics and automation tools.
Both approaches showcase the benefits of **integrated, automated workflows** for achieving efficiency, compliance, and global reach.
---