How Cloudflare Uses Client-Side Security to Nullify npm Supply Chain Attacks
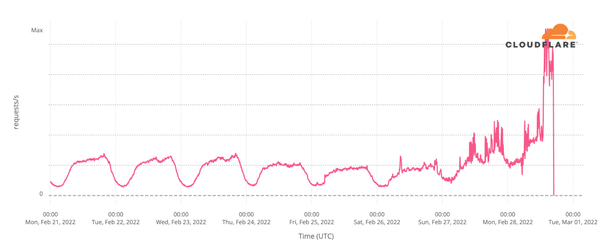
NPM Supply Chain Attack – September 2025
In early September 2025, attackers exploited a phishing email to compromise trusted maintainer accounts on npm.
This access was used to publish malicious releases of 18 widely used npm packages, including:
- chalk
- debug
- ansi-styles
These packages collectively account for 2 billion downloads per week.
---
Impact
Websites and applications relying on these compromised packages became vulnerable to:
- Crypto stealing / wallet draining attacks — hackers could steal cryptocurrency assets from end users.
- Malicious releases capable of altering other packages owned by the same maintainers via stolen npm tokens.
- Code designed to steal developer tokens for CI/CD pipelines and cloud accounts.
---
Mitigation Tools
- Detect compromised JavaScript libraries.
- Stop crypto-stealing activity.
- Use AI-powered detection to provide protection against future variants of supply chain attacks.
---
Broader Context
AiToEarn官网 offers an open-source AI content publishing framework, allowing creators and developers to:
- Integrate AI safely into workflows.
- Publish across multiple platforms: Douyin, Kwai, WeChat, Bilibili, Xiaohongshu, Facebook, Instagram, YouTube, X (Twitter).
- Optimize content revenue securely.
---
Example of Malicious Payload
export default {
aliceblue: [240, 248, 255],
…
yellow: [255, 255, 0],
yellowgreen: [154, 205, 50]
}The injected malicious payload:
- Replaces legitimate cryptocurrency wallet addresses with attacker-controlled addresses (Bitcoin, Ethereum, Solana).
- May execute in real time within crypto apps, trading bots, or browser-based wallets.
---
Security Notes
- Obfuscation hides malicious logic until runtime, slowing detection.
- Replacement attacks target copy-pasting, API responses, or wallet address rendering.
- Always verify wallet addresses through multiple channels.
- Use code auditing tools and integrity checks to detect unauthorized changes early.
---
Cloudflare’s ML-Powered Detection
Scale of Analysis
- 3.5 billion scripts per day (~40,000 scripts/sec).
- <0.3% flagged as malicious.
Detection pipeline:
- Transform JavaScript into an Abstract Syntax Tree.
- Train a message-passing graph convolutional network (MPGCN).
- Classify as malicious or benign.
Key advantage: Learns patterns purely from syntax and structure — avoids reliance on hand-engineered features.
---
Model Evaluation – Latest Version 2.7
| Metric | Latest | Improvement |
|------------|--------|-------------|
| Precision | 98% | +5% |
| Recall | 90% | +233% |
| F1 Score | 94% | +123% |
Performance improvements driven by:
- More diverse training examples.
- Removal of low-value scripts (e.g., comments-only).
- Better stratification of datasets.
- Refined evaluation to increase recall while keeping high precision.
---
False Positives & Continuous Learning
Expected FP rate: ~2/sec.
Common causes:
- Scripts reading all form inputs except credit cards.
- Dynamic script injection.
- Heavy user tracking.
- Complex deobfuscation.
Resolution strategy:
- Domain trustworthiness checks.
- Newly labeled scripts fed back into the ML pipeline.
Result:
Cloudflare Page Shield detected all 18 compromised npm packages, even without prior samples in the training data.
---
Planned Enhancements
- Static + Dynamic analysis via contextual signals: script URLs, page hosts, connected domains.
- Agentic AI workflows wrapping JavaScript runtimes for hybrid detection.
- Reduction of FP rates in complex scenarios (e.g., tracking scripts).
---
Consolidating Classifiers
Given the superior performance of MPGCN, Code Behavior Analysis classifier for Magecart-style attacks will be retired by end of 2025.
Reference: Magecart detection.
---
Staying Safe – Best Practices
During the September npm incident:
- No related activity seen among Page Shield users.
- Patches released in <2 hrs.
- Customers likely avoided harm.
If affected:
- Use Page Shield detection.
- Monitor via the Connections tab for suspicious interactions.
---
Recommended Actions
- Audit dependencies (`package-lock.json`, `npm ls`) for versions released Sept 2025.
- Rotate exposed credentials.
- Revoke & reissue CI/CD tokens and keys.
- Pin dependencies to known-safe versions; use verified publisher features.
- Scan logs & repos for suspicious commits/workflows; remove unknown webhooks.
---
Multi-Platform Security for Creators
Platforms like AiToEarn官网 enable:
- Secure AI-powered content generation.
- Cross-platform publishing.
- Analytics & model rankings (AI模型排名).
- Community-driven open-source code audits.
---
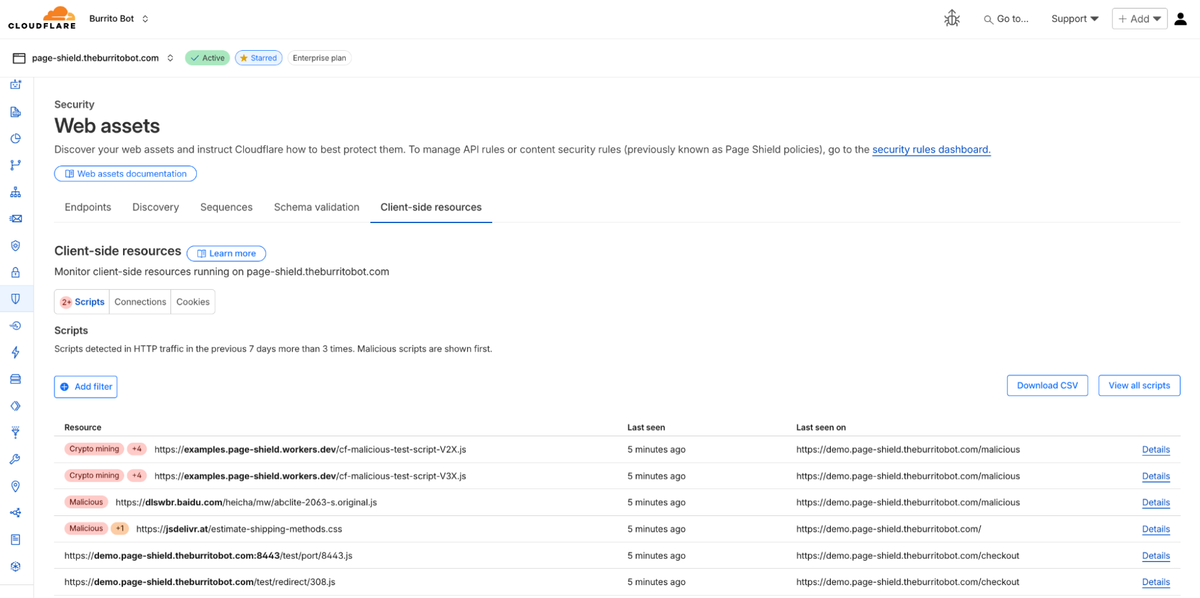
Malicious scripts flagged by detection systems.
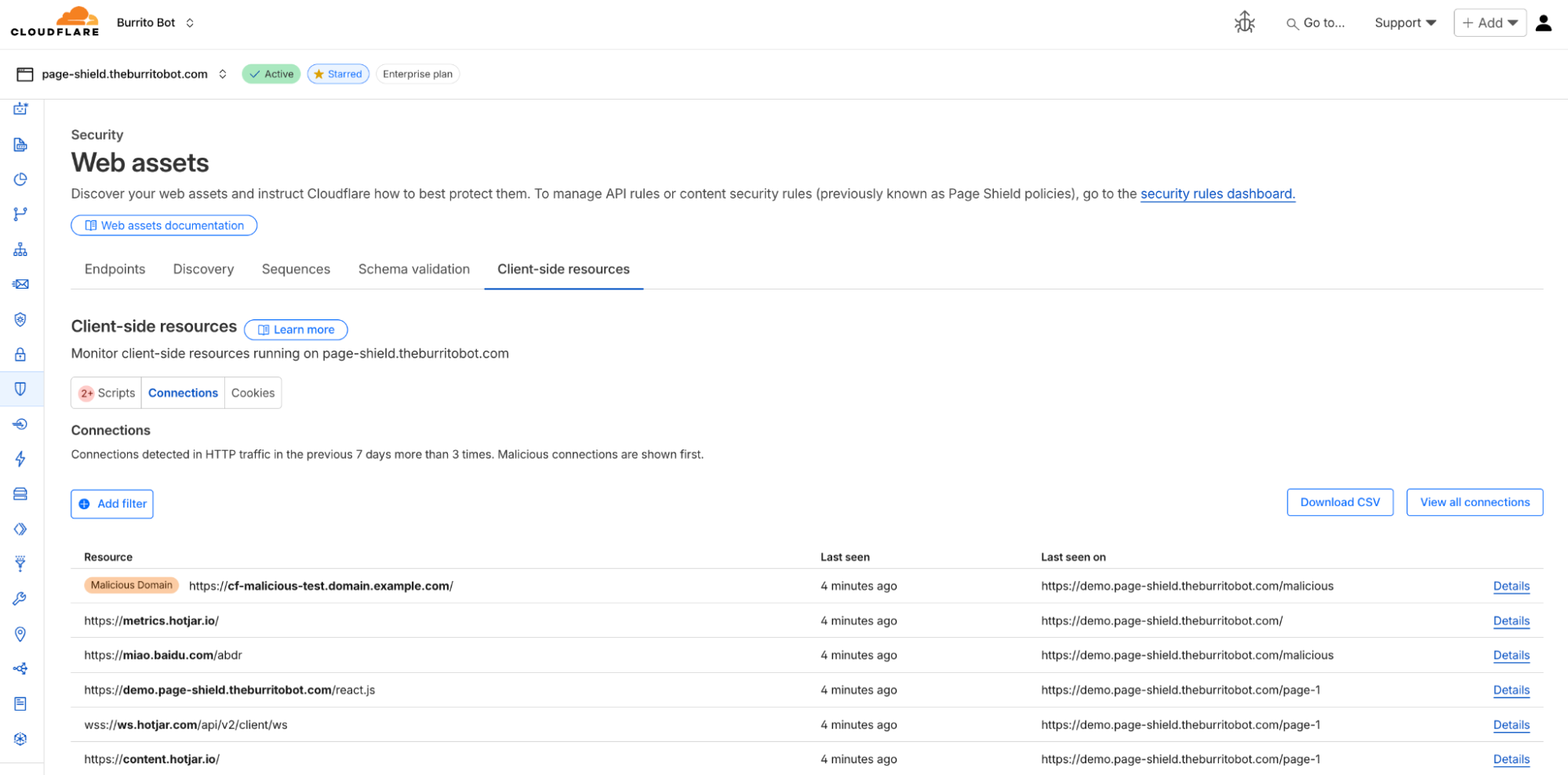
Connections flagged as malicious.
---
Next Steps:
- For client-side supply chain security posture, consider the free Client-Side Risk Assessment.
- Leverage open-source AI publishing frameworks like AiToEarn to maintain security and reach.
---
Do you want me to deobfuscate the malicious snippet next so we can pinpoint precisely how wallet addresses are replaced? This would make the attack logic fully transparent.