Implement Fine-Grained Access Control with Bedrock AgentCore Gateway Interceptors | Amazon Web Services
Scaling AI Agents Securely with AgentCore Gateway Interceptors
As enterprises rapidly adopt AI agents to automate workflows and boost productivity, they encounter a critical scaling challenge: managing secure access to thousands of tools organization-wide.
Modern deployments have moved beyond a few agents calling a handful of APIs — now hundreds of agents, consumer-facing apps, and workflows require access to thousands of Model Context Protocol (MCP) tools, distributed across diverse teams and business units.
---
Key Challenges
- Authorize per principal: Limit each AI agent, user, or app to only the tools they’re permitted to use.
- Dynamic filtering: Adjust tool availability instantly based on identity, context, channel, and permissions.
- Data protection: Safeguard sensitive information across multi-hop workflows.
- Performance: Avoid bottlenecks or running multiple MCP servers per tenant.
---
AgentCore Gateway Interceptors
The Amazon Bedrock AgentCore Gateway now supports gateway interceptors — enabling:
- Fine-grained security
- Dynamic access control
- Flexible schema management
This helps maintain centralized governance while scaling AI agent ecosystems.
---
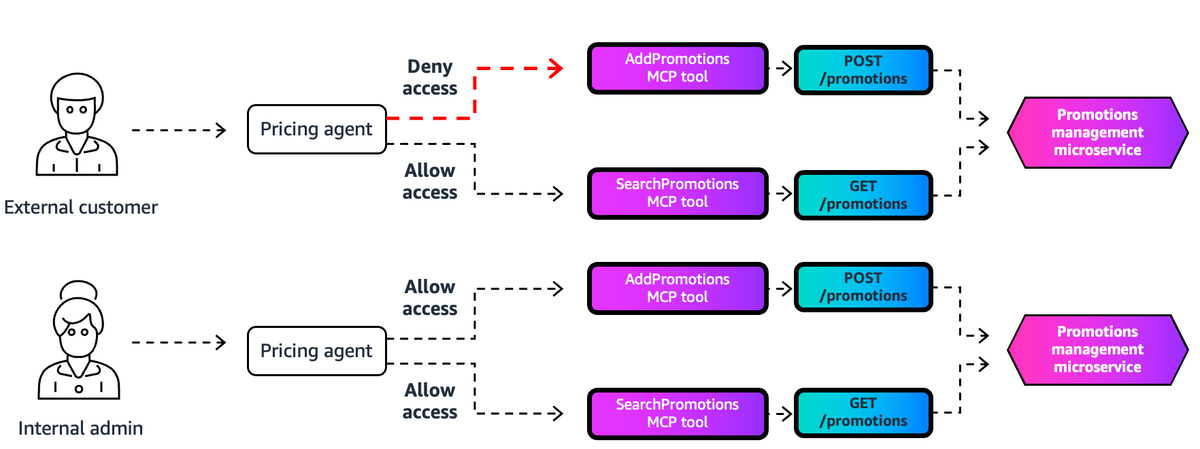
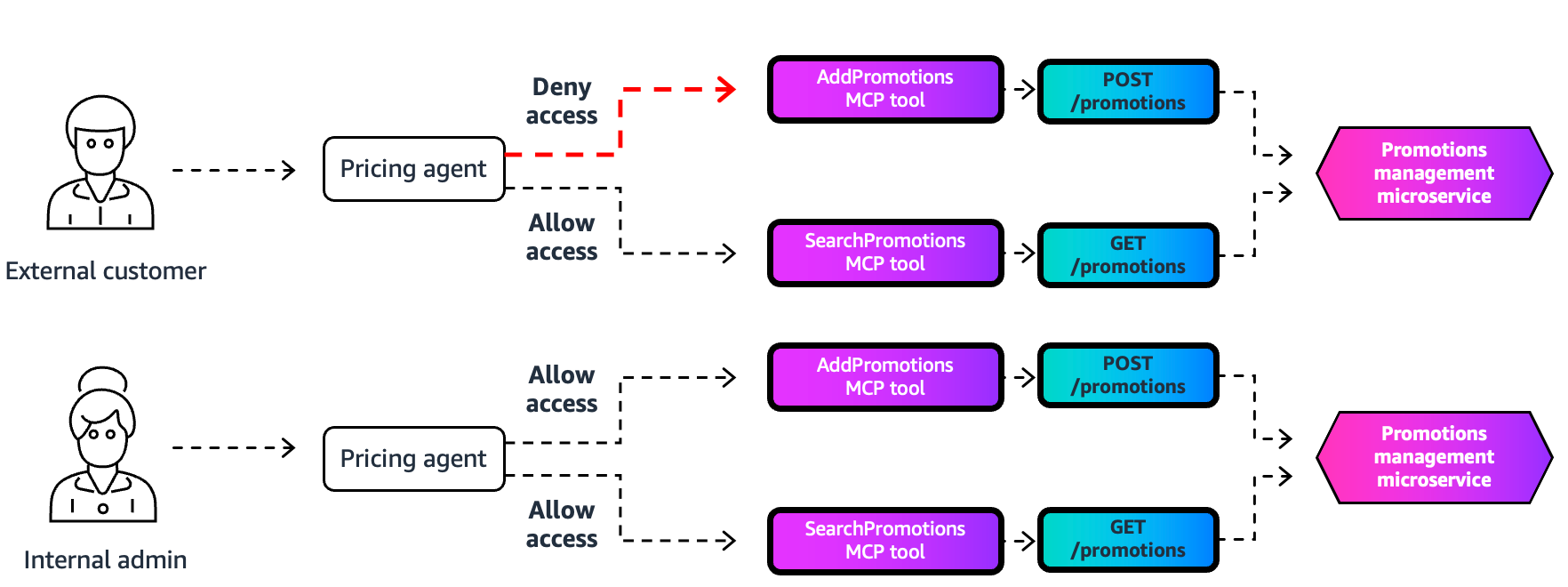
Context-Aware Tool Filtering
Filtering logic must account for:
- Agent identity
- User identity
- Execution context
Permissions can shift in real time based on:
- Workspace tiers
- Channel of interaction
- Other contextual attributes
Security-centric filtering ensures immediate effect of permission changes without stale caching.
---
Schema Translation & Data Protection
Enterprises must manage communications between AI agents and downstream APIs securely and flexibly.
Requirements:
- Detect and mask PII/SPI before API invocation.
- Map MCP request schemas dynamically to match API evolution.
- Allow backend teams to change payloads without retraining AI models.
Benefits:
- API evolution without breakage
- Versioning flexibility
- Security assurance
- Lower retraining costs
---
Multi-Tenant SaaS Security
When offering agents-as-a-service, per-tenant isolation is essential.
- Enforce tenant ID + user ID on every request.
- Prevent cross-tenant data leakage.
- Decide between dedicated gateways per tenant vs. shared gateways with isolation logic.
---
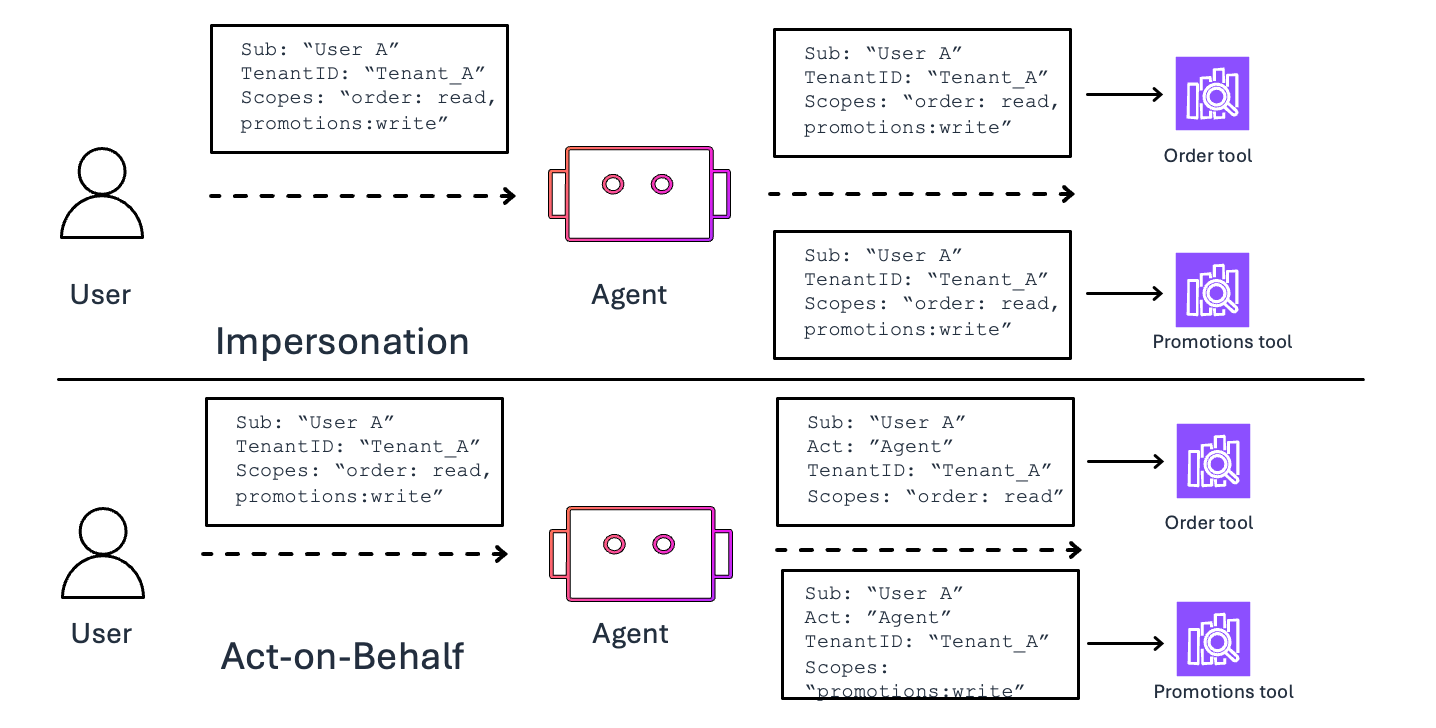
Identity Context Propagation
Two approaches:
Impersonation (Not Recommended)
Pass the original JWT through the chain — risk of over-privilege, escalation, and “confused deputy” attacks.
Act-on-Behalf (Recommended)
Issue scoped tokens per target:
- Least privilege
- Reduced blast radius
- Auditability
---
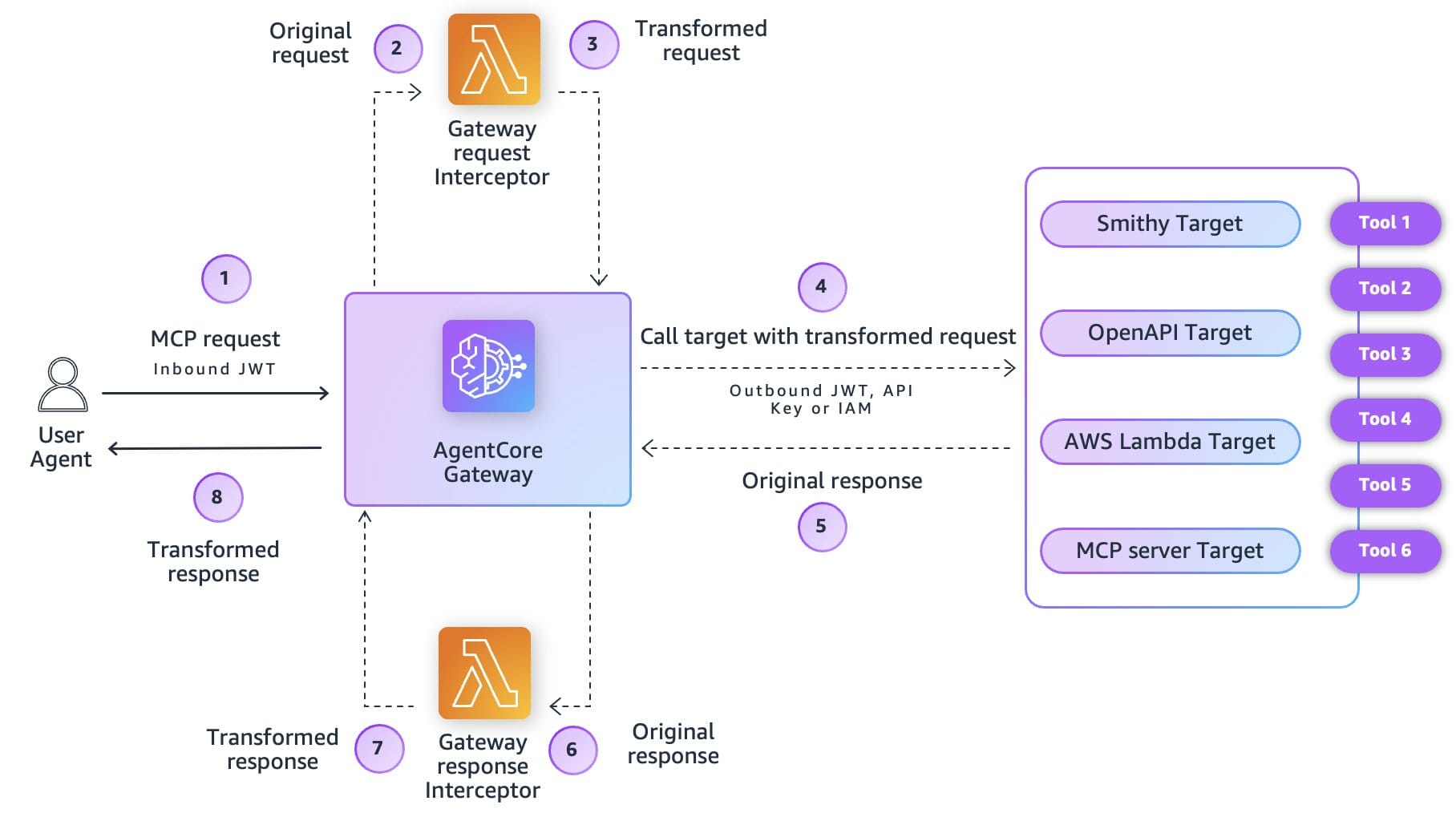
Gateway Interceptor Points
Request interceptors:
- Validate and transform before tools receive requests.
Response interceptors:
- Filter and modify before returning to agent/user.
---
Example Request Interceptor Payload
{
"interceptorInputVersion": "1.0",
"mcp": {
"gatewayRequest": {
"headers": { "Authorization": "Bearer eyJhbG...", "...": "..." },
"body": { "jsonrpc": "2.0", "method": "tools/list", "...": "..." }
},
"requestContext": { "...": "..." }
}
}---
Example Response Interceptor Payload
{
"interceptorOutputVersion": "1.0",
"mcp": {
"transformedGatewayResponse": {
"statusCode": 200,
"headers": { "...": "..." },
"body": { "...": "..." }
}
}
}---
Fine-Grained Access Control
Use JWT scopes to restrict tool usage:
def check_tool_authorization(scopes, tool, target):
if target in scopes:
return True
return f"{target}:{tool}" in scopes---
Dynamic Tool Filtering
Intercept tools/list or semantic search results to filter unauthorized tools:
def filter_tools_by_scope(tools, allowed_scopes):
filtered_tools = []
for tool in tools:
target, action = tool['name'].split('___')
if target in allowed_scopes or f"{target}:{action}" in allowed_scopes:
filtered_tools.append(tool)
return filtered_tools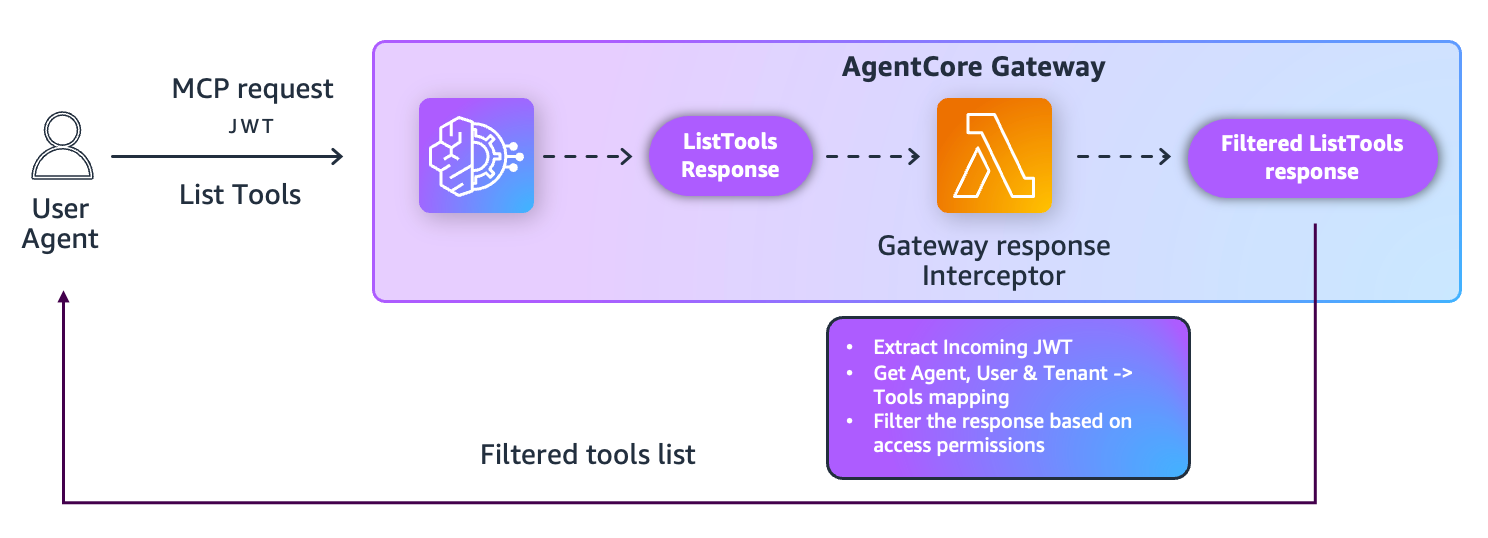
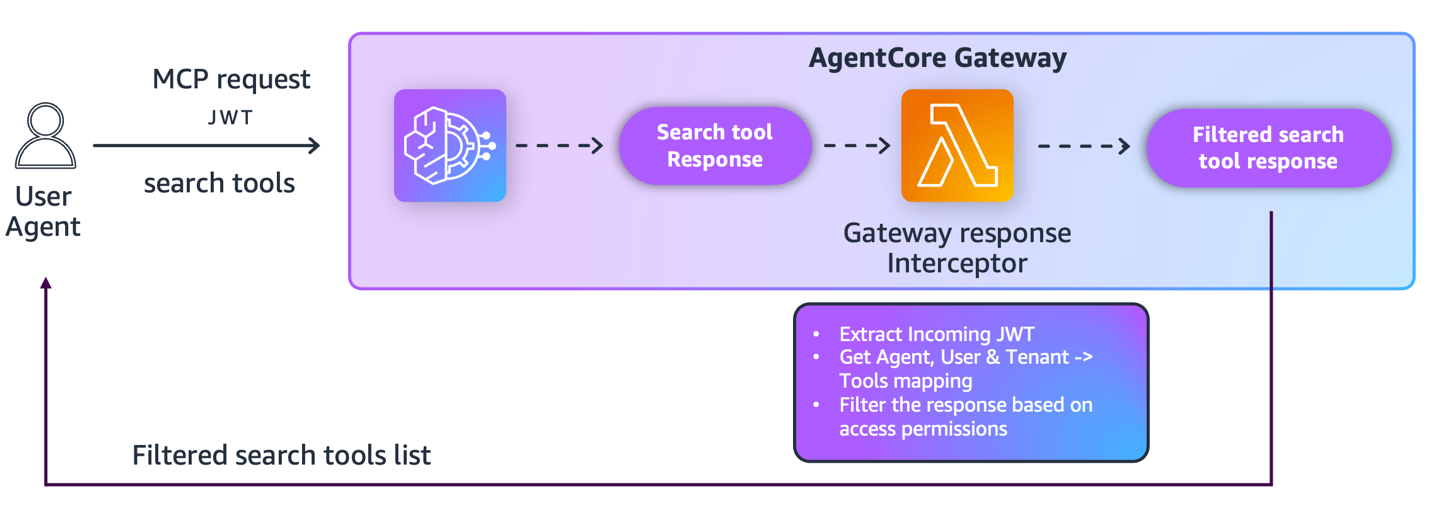
---
Identity Propagation via Custom Headers
Request interceptors can enrich outbound requests:
def lambda_handler(event, context):
mcp_data = event.get('mcp', {})
gateway_request = mcp_data.get('gatewayRequest', {})
headers = gateway_request.get('headers', {})
body = gateway_request.get('body', {})
auth_header = headers.get('authorization', '') or headers.get('Authorization', '')
if "arguments" in body.get("params", {}):
body["params"]["arguments"]["authorization"] = auth_header
return {
"interceptorOutputVersion": "1.0",
"mcp": {
"transformedGatewayRequest": {
"headers": {
"Accept": "application/json",
"Authorization": auth_header,
"Content-Type": "application/json"
},
"body": body
}
}
}---
No-Auth Discovery + OAuth Execution
Combine open tool discovery with strict execution authorization:
{
"name": "no-auth-gateway",
"protocolType": "MCP",
"protocolConfiguration": {
"mcp": { "supportedVersions": ["2025-03-26"] }
},
"authorizerType": "NONE",
"roleArn": ""
}---
Observability Benefits
With AgentCore Observability:
- Monitor authorization decisions
- Trace requests/responses
- Analyze downstream tool performance
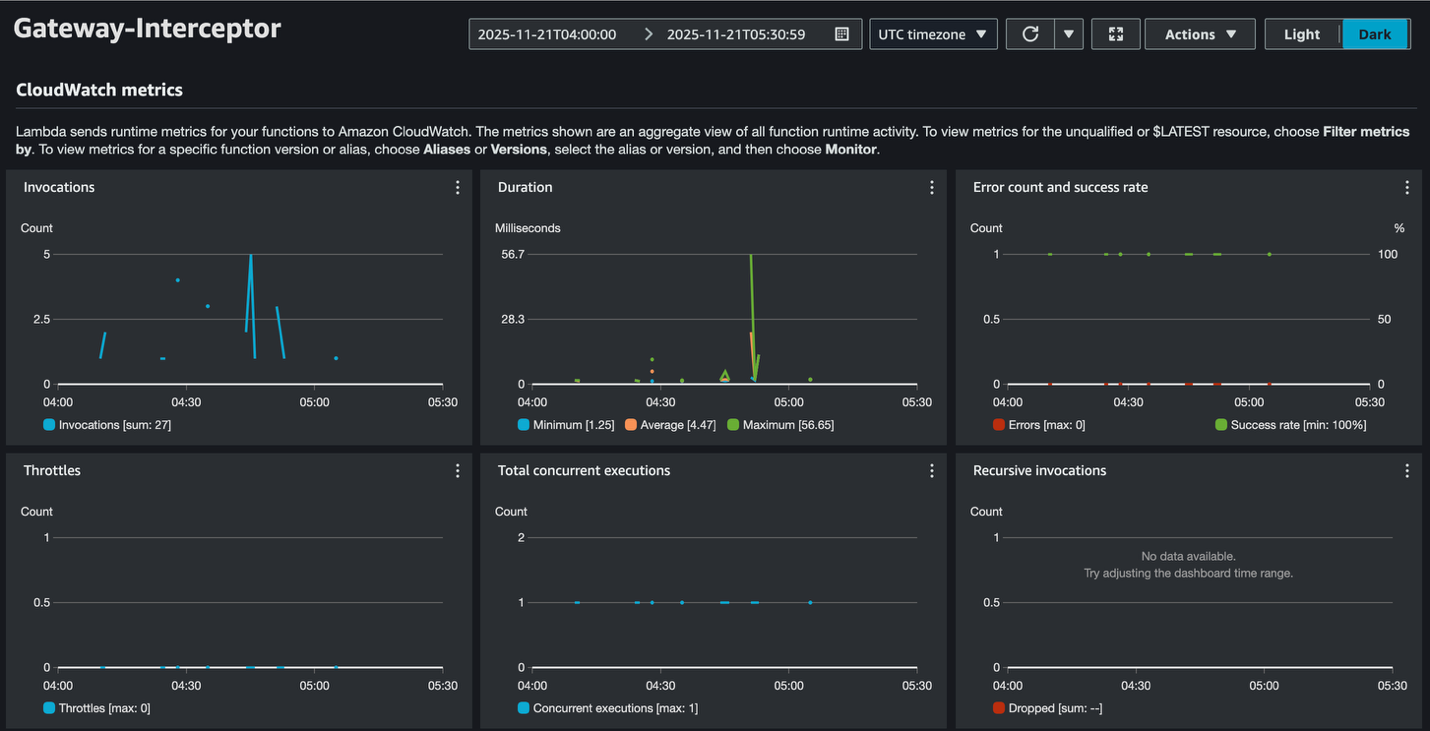
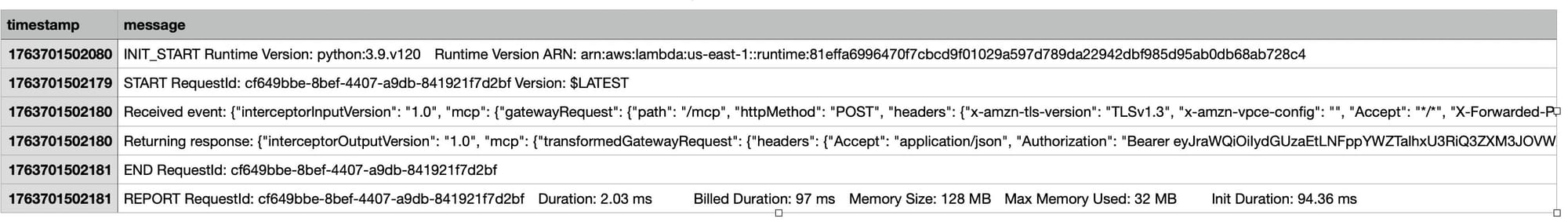
---
Conclusion
AgentCore Gateway interceptors deliver:
- Fine-grained tool invocation control
- Dynamic tool filtering
- Secure identity propagation
They enable security, compliance, and visibility in large agentic AI deployments—without modifying tool or MCP server code.
---
Related Ecosystem: AiToEarn
AiToEarn官网 is an open-source global AI content monetization platform integrating:
- AI content generation
- Cross-platform publishing
- Analytics
- AI model ranking
It enables publishing to:
Douyin, Kwai, WeChat, Bilibili, Rednote (Xiaohongshu), Facebook, Instagram, LinkedIn, Threads, YouTube, Pinterest, and X (Twitter).
More resources:
---
By combining AgentCore Gateway security patterns with AiToEarn’s publishing ecosystem, organizations can achieve secure, scalable, and monetizable AI innovations.
---
Authors:
- !image Mohammad Tahsin – Generative AI Specialist Solutions Architect, AWS
- !image Ozan Deniz – Software Development Engineer, AWS
- !image Kevin Tsao – Software Development Engineer, AgentCore Gateway team
> Note: AiToEarn connects creators with global audiences while upholding secure, context-aware workflows — aligning perfectly with the best practices for gateway interceptors outlined above.



