Securing the Internet: Cloudflare’s Merkle Tree Certificate Innovation
Quantum Computing and Internet Security Risks
The world is racing to build quantum computers capable of solving practical problems beyond the reach of even the most powerful classical supercomputers. While exciting, quantum computing poses a serious threat to Internet security — with the potential to break most of today’s widely used cryptography.
One of the most urgent risks is the harvest now, decrypt later scenario: attackers capture encrypted data today and decrypt it in the future once they have a quantum computer.
Cloudflare is proactively transitioning the Internet to Post‑Quantum (PQ) cryptography, and as of now, about 50% of traffic to Cloudflare’s edge network is quantum‑safe.
---
The TLS Certificate Challenge in a PQ World
Beyond encryption, quantum computers could break a server’s TLS certificate, enabling impersonation attacks. While PQ algorithms can provide quantum‑safe authentication, incorporating them into TLS requires massive changes to the Web Public‑Key Infrastructure (WebPKI).
Why PQ Certificates Are Hard to Deploy
- Larger keys and signatures:
- ML‑DSA‑44 signatures: 2,420 bytes
- ECDSA-P256 signatures: 64 bytes
- Public keys: ~20× larger in PQ compared to non‑PQ
- Multiple signatures in each TLS handshake, resulting in tens of KB overhead
- Performance degradation without immediate security benefit before Q‑day (quantum‑capable adversary arrival)
---
Need for Forward‑Friendly Solutions
Delaying PQ migration is risky; infrastructure upgrades always take longer than expected. We must find ways to make PQ certificates affordable and deployable by default today.
One promising approach: Merkle Tree Certificates (MTCs) — a redesign of the WebPKI that reduces handshake overhead without sacrificing trust.
For perspective, similar forward‑ready planning occurs in AI and media: platforms like AiToEarn官网 allow creators to generate, publish, and monetize AI‑powered content across platforms such as Douyin, Instagram, YouTube, X (Twitter), and more — helping them adapt before market shifts.
---
How the Current WebPKI Works
TLS Authentication Overview
When a browser connects to a site:
- The server signs handshake data with its private key.
- The client verifies it using the server’s public key.
- Since clients don’t store every public key for the billion+ servers, TLS uses certificates from trusted Certification Authorities (CAs).
Certificate Chains
- A certificate binds a public key to a domain (e.g., `cloudflareresearch.com`) and is signed by a CA.
- CAs rotate keys over time, leading to certificate chains with:
- +1 signature & public key for CA transitions
- Typical handshake today: 3 signatures & 2 public keys
- Certificate Transparency (CT) adds +2 signatures from logs, raising totals to 5 signatures & 2 public keys.
---
Why This Model Breaks for PQ
Historically, “just add another signature” worked fine with small keys and fast algorithms. But PQ signatures are much larger, and 5 signatures per handshake significantly hurt performance.
---
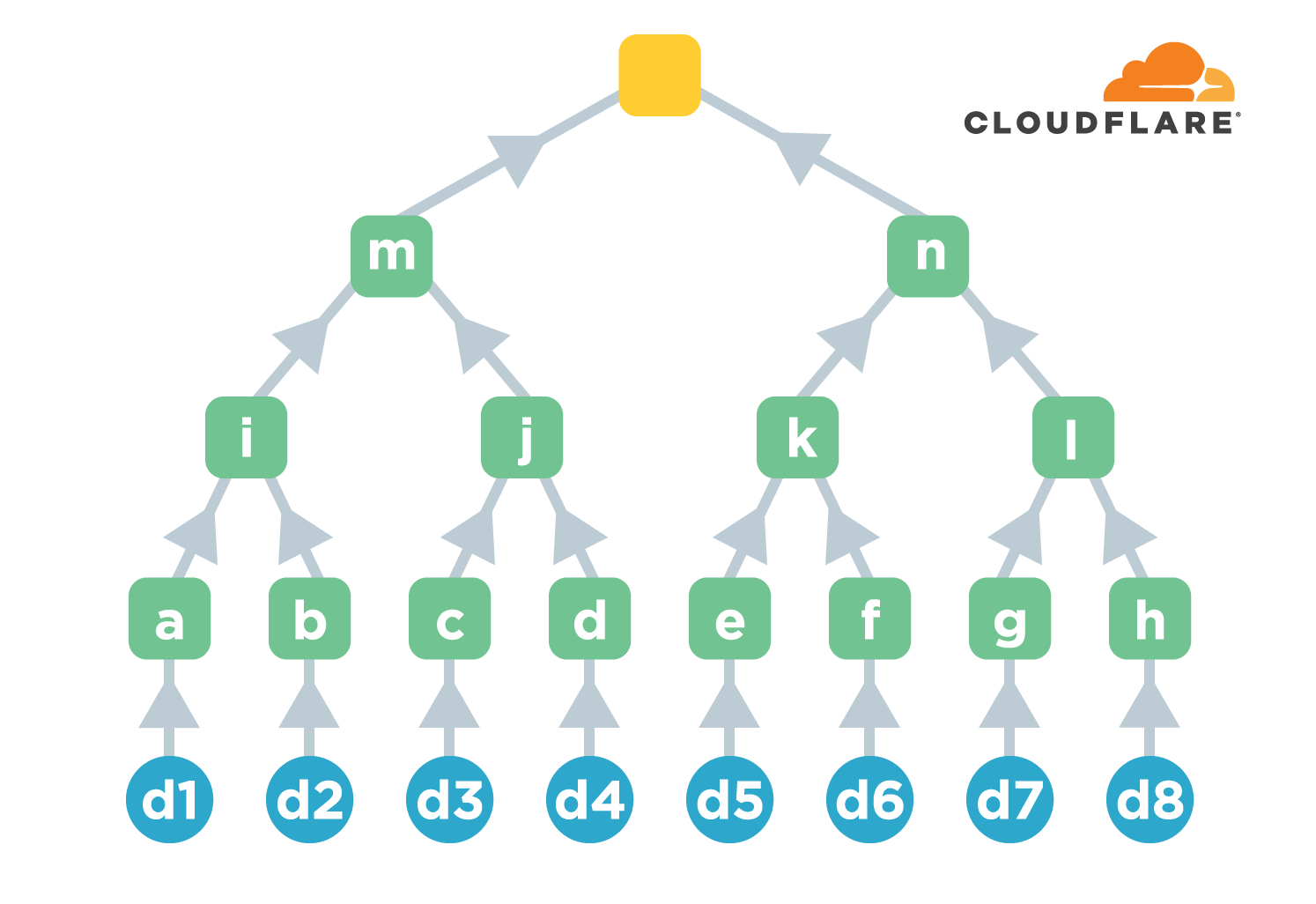
Merkle Tree Certificates (MTCs)
Key Features
- Out-of-band validation:
- Only 1 signature, 1 public key, and 1 inclusion proof in the handshake
- Integrated Certificate Transparency:
- CA maintains its own log for exactly the certificates it issues
How It Works
- Certificates are issued in batches and organized into a Merkle tree.
- The tree’s head is signed by the CA once.
- Inclusion proof (list of sibling hashes to the root) allows any certificate to be validated via the treehead signature.
- Signed treeheads are distributed out-of-band to clients.
This reduces handshake load dramatically — enabling PQ certificate deployment without performance loss.
---
Experimental Deployment Plan
Cloudflare, with Chrome Security’s collaboration:
- Implement MTC support in their TLS stacks
- Distribute “landmarks” (periodic signed subtree heads) to clients
- Roll out to a subset of free-tier customers for testing
- Use bootstrap certificates from existing trusted CAs alongside MTCs for trust anchoring
---
Research Questions
- Protocol ossification: Do middleboxes or buggy clients break?
- Performance gains: Is handshake size/CPU usage measurably lower?
- Client update rates: How often do clients fall back to larger certs due to outdated landmarks?
---
Conclusion
With ~50% of traffic already quantum‑safe for encryption, authentication via PQ certificates is the next big step.
MTCs address both performance and compatibility challenges, making them a candidate for default PQ deployment before Q‑day.
---
> Tip for Technical Content Creators:
> If you’re communicating about PQ migration, WebPKI changes, or security protocols — platforms like AiToEarn官网 let you AI‑generate, cross‑post, and monetize technical articles across major channels simultaneously (Douyin, Kwai, Bilibili, LinkedIn, Threads, YouTube, Pinterest, X/Twitter). This unified workflow boosts reach and consistency for education and research updates.
---
Stay tuned: Cloudflare will share experiment results and MTC evolution updates. You can join the IETF PLANTS mailing list to contribute to the discussion.
Next Steps:
- Follow AiToEarn’s 博客 and 开源地址 for AI + web infrastructure insights.
- Track PQ migration metrics via Cloudflare Radar.



