Strix: An Open-Source AI Agent Revolutionizing Security Testing
# Strix: An AI-Powered Ethical Hacker for Developers
Every developer knows the feeling: you deploy an update, everything seems fine — and then that little voice inside whispers, *“But is it secure?”*
You’ve run unit tests, the linter is clean, and code reviews are green.
Yet, deep down, you suspect there might still be risks:
- An input validation missing somewhere.
- A route exposing sensitive data.
The problem?
**Traditional security testing is slow and noisy**:
- Penetration tests can take weeks.
- Static analyzers often produce hundreds of false positives.
- Many tools are cumbersome and disrupt the developer workflow.
[**Strix**](https://github.com/usestrix/strix) changes that.
It’s an **open-source AI-driven “hacker”** — one that behaves like a real attacker, runs your code, probes endpoints, and verifies vulnerabilities by safely exploiting them. Strix is built to work **with** developers, not against them.
In this guide, you’ll learn:
- How Strix works.
- How to install and run it.
- Real-world vulnerability examples.
- How its AI agents reason.
- How to integrate it seamlessly into your workflow.
---
## Table of Contents
- [Prerequisites](#heading-prerequisites)
- [The Problem Developers Face](#heading-the-problem-developers-face)
- [The Strix Approach](#heading-the-strix-approach)
- [How to Install Strix](#heading-how-to-install-strix)
- [Working with Strix](#heading-working-with-strix)
- [Example: Insecure Direct Object Reference](#heading-example-insecure-direct-object-reference-idor)
- [Example: Remote Code Execution via Unsafe Deserialization](#heading-example-remote-code-execution-rce-via-unsafe-deserialization)
- [How Strix Thinks](#heading-how-strix-thinks)
- [Developer-Friendly Design](#developer-friendly-design)
- [Local, Private Execution](#local-private-execution)
- [Enterprise Platform](#heading-enterprise-platform)
- [Why Strix Matters](#heading-why-strix-matters)
- [The Future of AI Security](#heading-the-future-of-ai-security)
- [Conclusion](#heading-conclusion)
---
## Prerequisites
Before diving in, make sure you have:
- [Basic knowledge of Python](https://www.freecodecamp.org/news/learn-python-basics/)
- [**Familiarity with Docker**](https://www.freecodecamp.org/news/how-docker-containers-work/)
Strix runs its tests inside **isolated Docker containers**. Knowing the basics of images and containers will help.
- **An AI provider key**
Strix uses LLMs (Large Language Models) to reason about vulnerabilities. Get an API key from OpenAI, Anthropic, or another supported provider.
---
## The Problem Developers Face
Modern development ships features fast, but **security testing lags behind**:
- Release cycles are frequent.
- Security assessments are slow and detached from day-to-day coding.
- Tools raise “possible” vulnerabilities, leaving devs to spend hours verifying.
**Developers need proof, not guesses.**
Strix delivers that proof via AI reasoning and exploit verification, letting teams focus on real issues.
---
## The Strix Approach
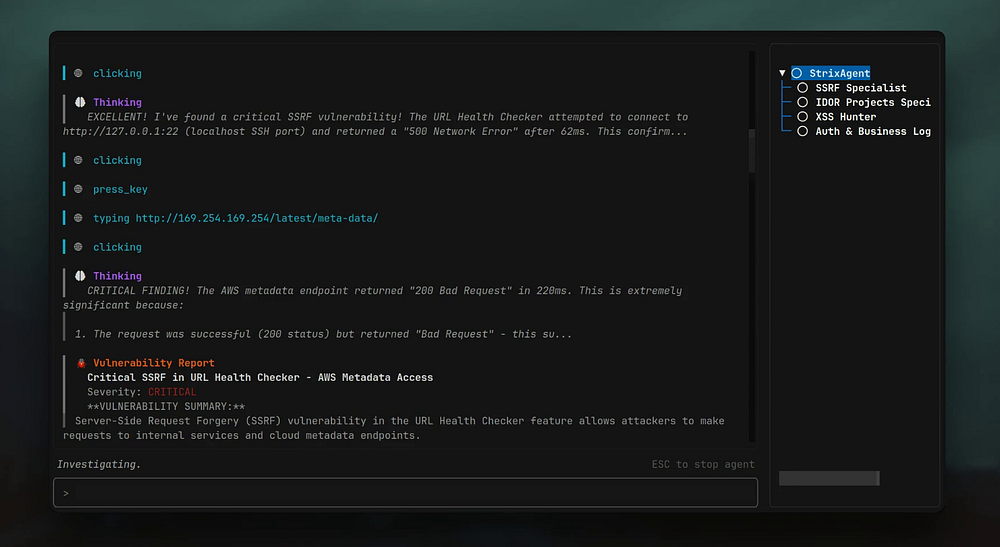
Strix is **not just a scanner** — it’s a suite of autonomous AI agents behaving like skilled hackers:
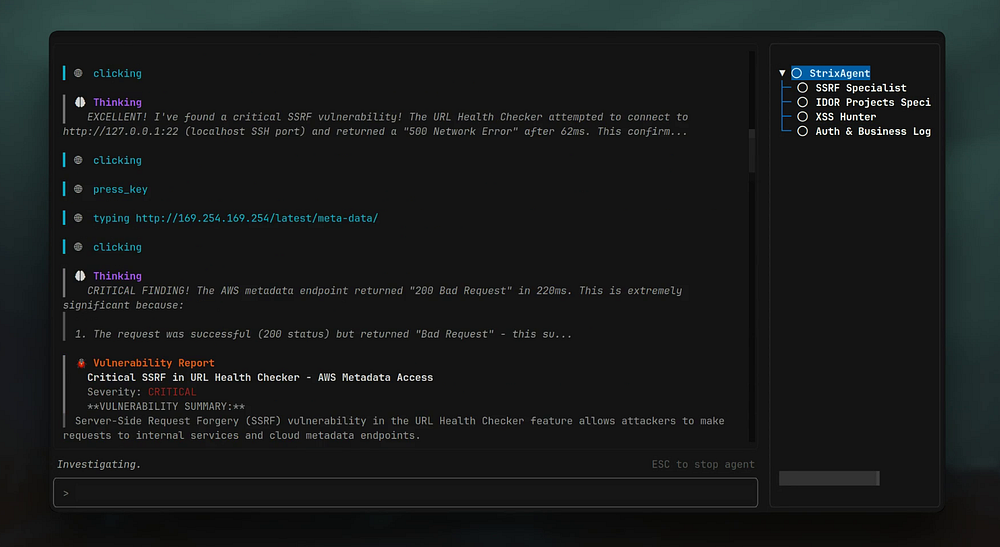
**Core capabilities:**
- Map your application.
- Attack endpoints.
- Verify vulnerabilities with working proof-of-concepts.
Instead of vague warnings, Strix tells you:
- Exactly what happened.
- Where it happened.
- How to fix it.
It’s like having a tireless, automated security team embedded in your dev workflow.
---
## How to Install Strix
**Requirements:**
- [Docker](https://www.docker.com/)
- Python 3.12+
- LLM provider key
**Installation via `pipx`:**pipx install strix-agent
**Configuration Example (OpenAI):**export STRIX_LLM="openai/gpt-5"
export LLM_API_KEY="your-api-key"
---
## Working with Strix
**Basic command:**strix --target ./app
What happens:
1. Strix creates an **isolated sandbox** via Docker.
2. Multiple AI agents collaborate:
- **Scan routes**
- **Send requests**
- **Inject payloads**
- **Interpret responses**
3. If a vulnerability looks real, Strix:
- Generates an exploit.
- Executes it safely in the sandbox.
- Confirms viability.
**Outputs:**
- Detailed logs
- Proof-of-concept exploits
- Recommended fixes
All stored locally — **real, tested, reproducible results**.
---
## Example: Insecure Direct Object Reference (IDOR)
**Scenario:**
API returns user invoices by numeric ID:GET /invoices/123
Authorization: Bearer
**Issue:**
No ownership checks. A user can access another’s invoices by changing the ID.
**Strix Process:**
1. Recon agent maps the route.
2. Auth agent tests token behavior.
3. Attempts:GET /invoices/124
using *User A’s* token.
4. If *User B’s* data is returned → IDOR confirmed.
**Report Includes:**
- Successful request
- Vulnerable resource IDs
- Fix suggestions:
- Enforce ownership checks server-side.
- Map IDs to user scope.
---
## Example: Remote Code Execution (RCE) via Unsafe Deserialization
**Vulnerable Python endpoint:**@app.post("/jobs")
def create_job(payload: bytes):
job = pickle.loads(payload)
job.run()
return {"status": "queued"}
**Risk:**
Untrusted input is deserialized → arbitrary code execution possible.
**Strix Process:**
- Runs service in safe Docker sandbox.
- Generates harmless payload triggering an action.
- Confirms execution.
**Report Includes:**
- Result of execution.
- Serialized proof-of-concept.
- Output generated.
**Best Practices to Avoid RCE:**
- Use safe formats like JSON.
- Validate all inputs.
- Restrict permissions for any deserialization.
---
## How Strix Thinks
- Operates via a **coordination graph**.
- Different agents handle:
- Endpoint mapping.
- Payload creation.
- Exploit documentation.
- Agents share results and adapt strategies.
This is **a team of digital security testers** working in concert.
---
## Developer-Friendly Design
- **CLI-based** → no heavy dashboards.
- Can scan:
- Local projects.
- GitHub repos.
- Live applications.
- Reports stored in `agent_runs`:
- Clear description.
- Confirmed exploit details.
- Step-by-step remediation.
---
## Local, Private Execution
- Runs locally at **no cost**.
- All data stays on your machine.
- No code or sensitive data leaves your environment.
---
## Enterprise Platform
Designed for large teams managing many projects:
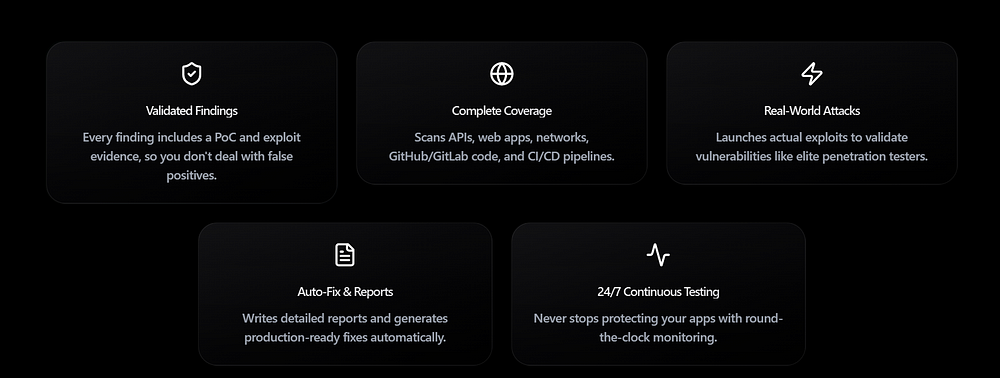
**Features:**
- Vulnerability dashboards across projects.
- Large-scale parallel scanning.
- CI/CD integrations.
- Jira & Slack integrations.
- Custom fine-tuned AI models from your own data.
**Benefits:**
- Real-time collaboration between devs and security teams.
- Security testing embedded throughout the SDLC.
---
## Why Strix Matters
- Brings real-world hacking techniques into dev workflows.
- Delivers **proof, not theory**.
- Allows vulnerability detection in minutes, not weeks.
- Saves time, reduces stress, improves code confidence.
---
## The Future of AI Security
Strix is part of a new wave of **autonomous, intelligent security testers**.
As AI models get smarter:
- They’ll understand complex systems better.
- Adapt attack strategies dynamically.
- Closely resemble automated unit tests/linting in terms of developer workflow integration.
---
## Conclusion
Strix turns AI into your **personal ethical hacker**:
- **Scans** applications.
- **Detects & verifies** vulnerabilities.
- **Provides fixes**.
- Works locally, in CI, or at enterprise scale.
For developers, this means faster feedback, stronger code integrity, and fewer production surprises.
---
*For more hands-on tutorials on AI, subscribe to the free AI newsletter* [***TuringTalks.ai***](https://www.turingtalks.ai/) *or visit* [***my website***](https://manishshivanandhan.com/)*.*