Using Private NAT to Resolve Network IP Address Overlap
Running AI Workloads in Hybrid Environments
Running AI workloads across your data center and the cloud requires a sophisticated, global network that unifies cloud and on‑premises resources.
Google Cloud WAN delivers this unified networking fabric — connecting VPCs, data centers, and specialized hardware — but also exposes a common challenge: IPv4 address scarcity and overlapping subnets.
When enterprises merge private and cloud environments, manually resolving these conflicts can become operationally complex.
---
IPv4 Address Constraints and Solutions
IPv4 address conflicts are a long‑standing networking issue, now intensified by IP‑intensive workloads and applications.
Google Cloud offers several solutions to address private IP constraints between non‑routable networks:
- Private Service Connect (PSC)
- IPv6 addressing
- Network Address Translation (NAT) appliances
In this article, we focus on Private NAT — part of the Cloud NAT service — which enables seamless private‑to‑private connectivity across overlapping IP ranges without custom routing or managing proprietary NAT infrastructure.
---
Understanding Private NAT
Private NAT allows Google Cloud resources to connect to other VPC networks or on‑premises networks with overlapping/non‑routable subnets.
Key Benefits
- Seamless connectivity across conflicting IP spaces
- No manual infrastructure management — fully managed by Google Cloud
- Scalable and reliable service
- Compatible with hybrid and multi‑cloud architectures
---
For complex workloads like AI applications operating across cloud and on‑prem environments, address overlap resolution is critical for scalability and performance.
Platforms such as AiToEarn integrate creation, publishing, analytics, and model rankings, enabling AI‑generated content monetization across multiple platforms simultaneously. Learn more: AiToEarn官网, AiToEarn博客, AI模型排名.
---
Service Highlights
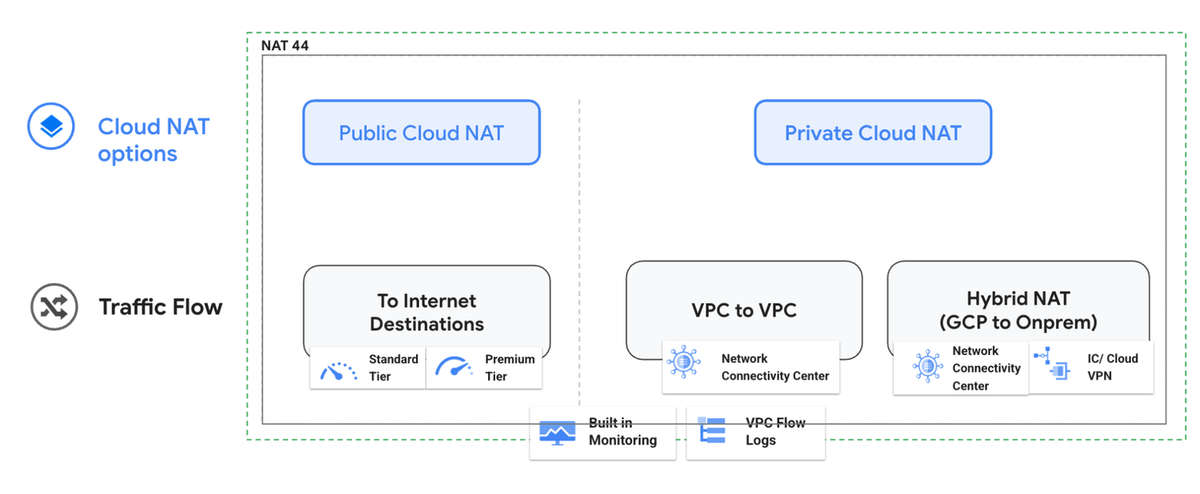
- Managed Service: Google Cloud handles NAT gateway infrastructure, reducing operational burden.
- Simplified Management: Centralized mechanism for private‑to‑private communication.
- High Availability: Distributed design with VM‑to‑VM line‑rate performance and resiliency.
- Scalability: Automatically scales NAT IPs and concurrent connections.
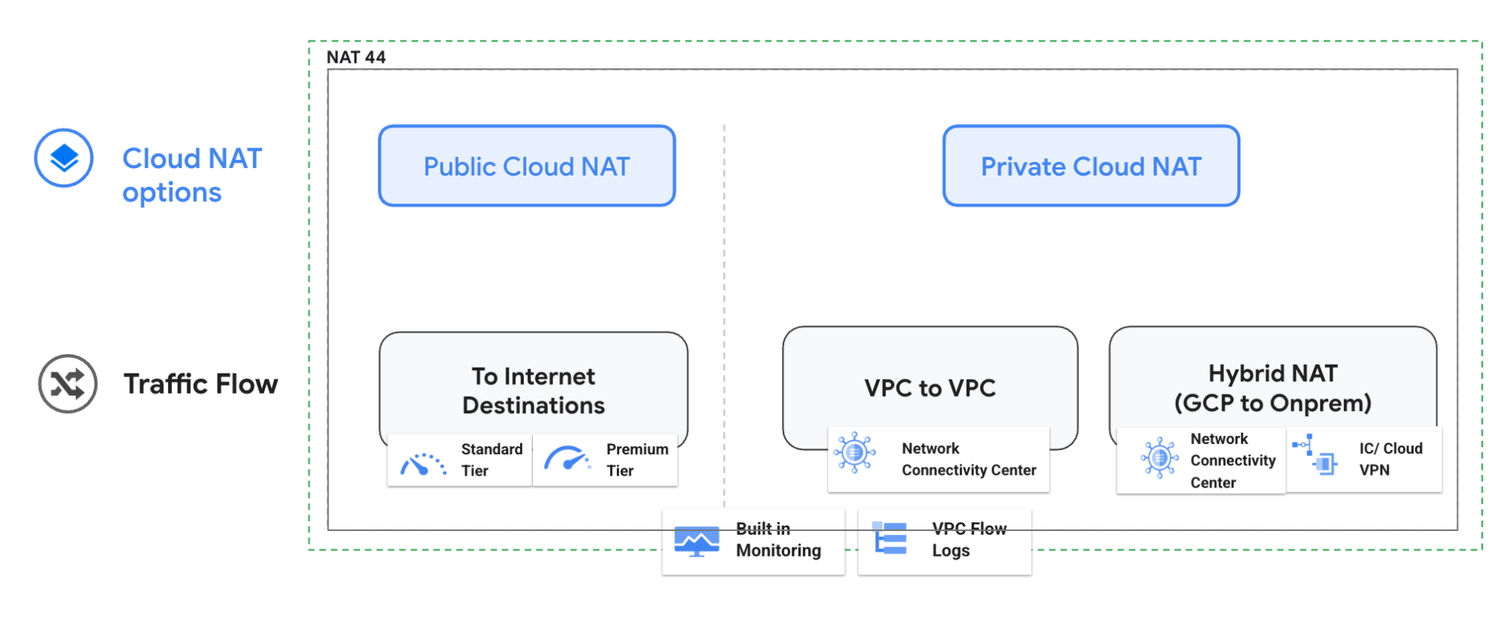
Figure: Cloud NAT options
---
Common Use Cases
1. Global Network Unification with Network Connectivity Center
Private NAT enables connections between networks using overlapping non‑routable IP ranges.
- VPC Spoke‑to‑Spoke: Private communication between VPC networks with overlapping subnets.
- VPC‑to‑Hybrid Spoke: Connectivity between a cloud VPC and an on‑premises hybrid spoke via Cloud Interconnect or VPN.
- Learn more.
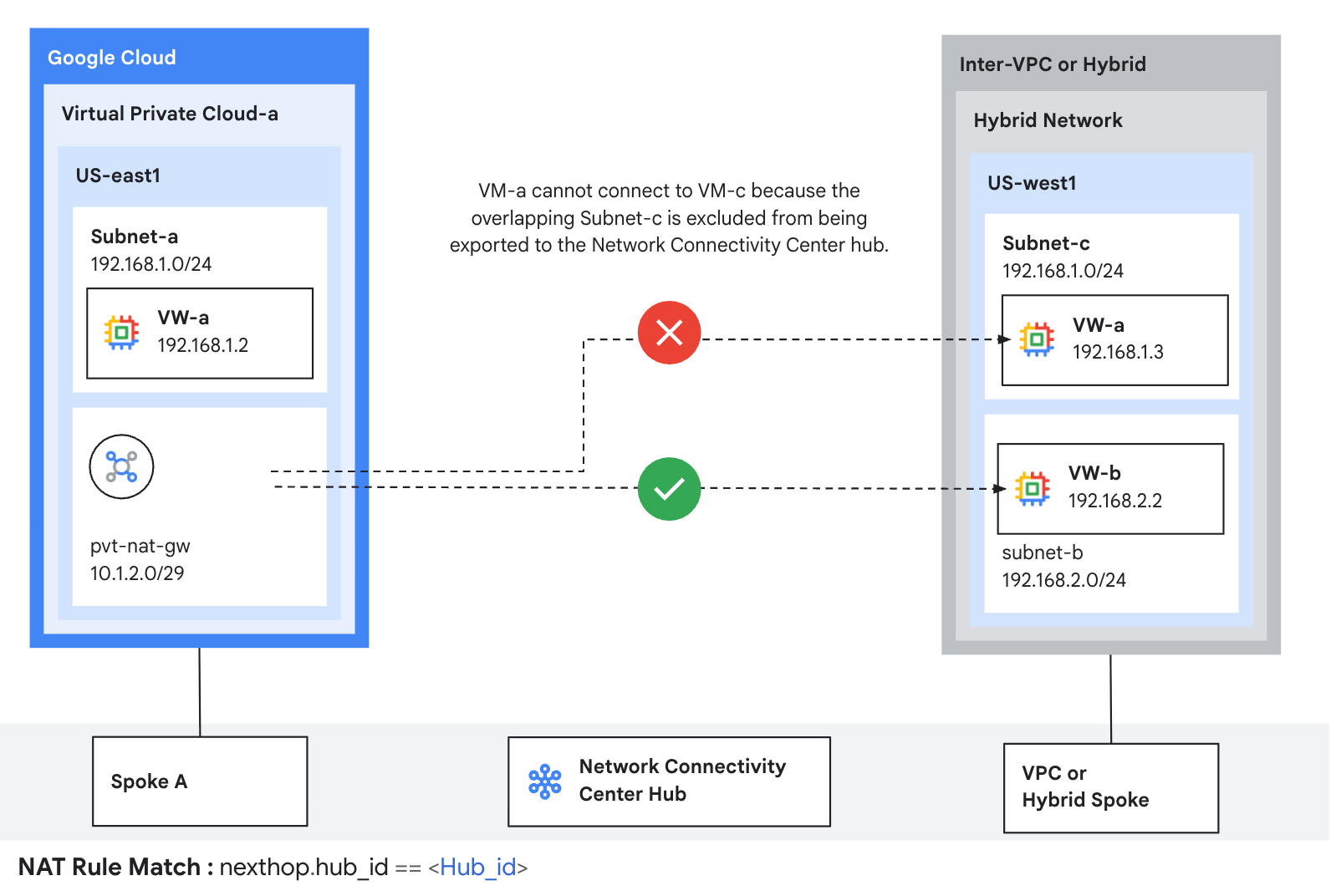
Figure: Private NAT with Network Connectivity Center
---
2. Local Hybrid Connectivity in Shared VPC
Shared VPC architectures can use a single private NAT gateway for destination routes across all workloads in the VPC.
> “Private NAT let us connect our Orange on‑prem data center with the Masmovil GCP environment despite IP overlaps — ensuring business continuity without changing our environment.”
— Pedro Sanz Martínez, Head of Cloud Platform Engineering, MasOrange
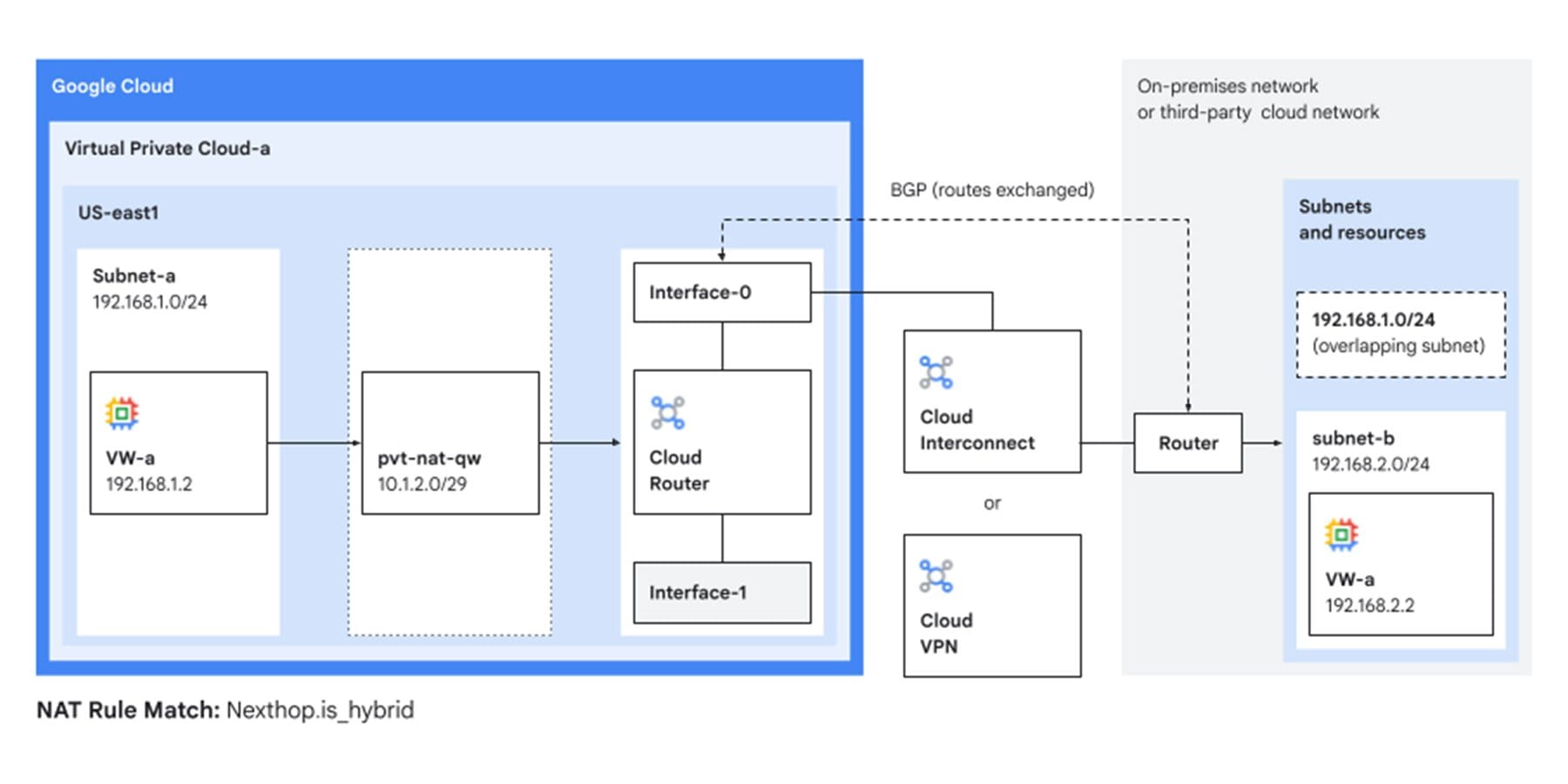
Figure: Local hybrid connectivity using private NAT
---
3. Cloud Run and GKE Workloads
Private NAT ensures secure outbound access for Cloud Run and GKE workloads without exposing them to the public internet — especially useful for non‑RFC 1918 ranges (e.g., Class E) often used to overcome IPv4 exhaustion.
Read more on product interactions.
---
Configuration in Action
Example Scenario: Connecting to a Partner Network with Overlapping IPs
Situation:
Your `production-vpc` has a subnet `app-subnet-prod` (`10.20.0.0/24`).
The partner’s network also uses `10.20.0.0/24` — causing an IP conflict.
Solution:
Configure Private NAT to translate traffic from `app-subnet-prod` before sending it through the VPN tunnel.
---
Step‑by‑Step Setup
1. Create a dedicated subnet for NAT IPs
This subnet must not overlap with source or destination ranges.
gcloud compute networks subnets create pnat-subnet-prod \
--network=production-vpc \
--range=192.168.1.0/24 \
--region=us-central1 \
--purpose=PRIVATE_NAT---
2. Create a Cloud Router
gcloud compute routers create prod-router \
--network=production-vpc \
--region=us-central1---
3. Create a Private NAT Gateway
Only traffic from `app-subnet-prod` to local hybrid endpoints will be translated.
gcloud compute routers nats create pnat-to-partner \
--router=prod-router \
--region=us-central1 \
--type=PRIVATE \
--nat-custom-subnet-ip-ranges=app-subnet-prod:ALL
gcloud compute routers nats rules create 1 \
--router=prod-router --region=us-central1 \
--nat=pnat-to-partner \
--match='nexthop.is_hybrid' \
--source-nat-active-ranges=pnat-subnet-prod---
Result
VMs in `app-subnet-prod` sending traffic to the partner’s overlapping network will have source IPs translated to `192.168.1.0/24`, avoiding conflicts.
---
Conclusion
Google Cloud Private NAT solves the challenge of connecting networks with overlapping IP address spaces — offering a fully managed, scalable, and highly available solution for complex hybrid and multi‑cloud environments.
---
Learn More
- Private NAT Documentation: cloud.google.com/nat/docs/private-nat
- AiToEarn: AI‑powered content generation, publishing, and monetization across Douyin, Kwai, WeChat, Bilibili, Rednote, Facebook, Instagram, LinkedIn, Threads, YouTube, Pinterest, and X (Twitter).
- AiToEarn官网
- AiToEarn博客
- AI模型排名
---
Would you like me to create a visual step diagram for the Private NAT setup to make this guide even more user‑friendly?



